mirror of
https://github.com/outbackdingo/firezone.git
synced 2026-01-27 18:18:55 +00:00
Minor docs fixes (#505)
* Minor docs fixes * MD012 fix Co-authored-by: Jason Gong <jason@firez.one>
This commit is contained in:
@@ -95,7 +95,7 @@ cd ../..
|
||||
mix start
|
||||
```
|
||||
|
||||
At this point you should be able to log into
|
||||
At this point you should be able to sign in to
|
||||
[http://localhost:4000](http://localhost:4000) with email `factory@factory` and
|
||||
password `factory`.
|
||||
|
||||
|
||||
@@ -1,5 +1,8 @@
|
||||
{%- if site.footer_content -%}
|
||||
<div class="text-small mb-0">
|
||||
<p>
|
||||
WireGuard® is a registered trademark of Jason A. Donenfeld.
|
||||
</p>
|
||||
<p>
|
||||
For support, first visit our
|
||||
<a href="https://discourse.firez.one/">Discussion Forums</a>
|
||||
|
||||
@@ -21,9 +21,16 @@ If you wish to use an OAuth provider that is not listed above,
|
||||
please open a
|
||||
[GitHub issue](https://github.com/firezone/firezone/issues).
|
||||
|
||||
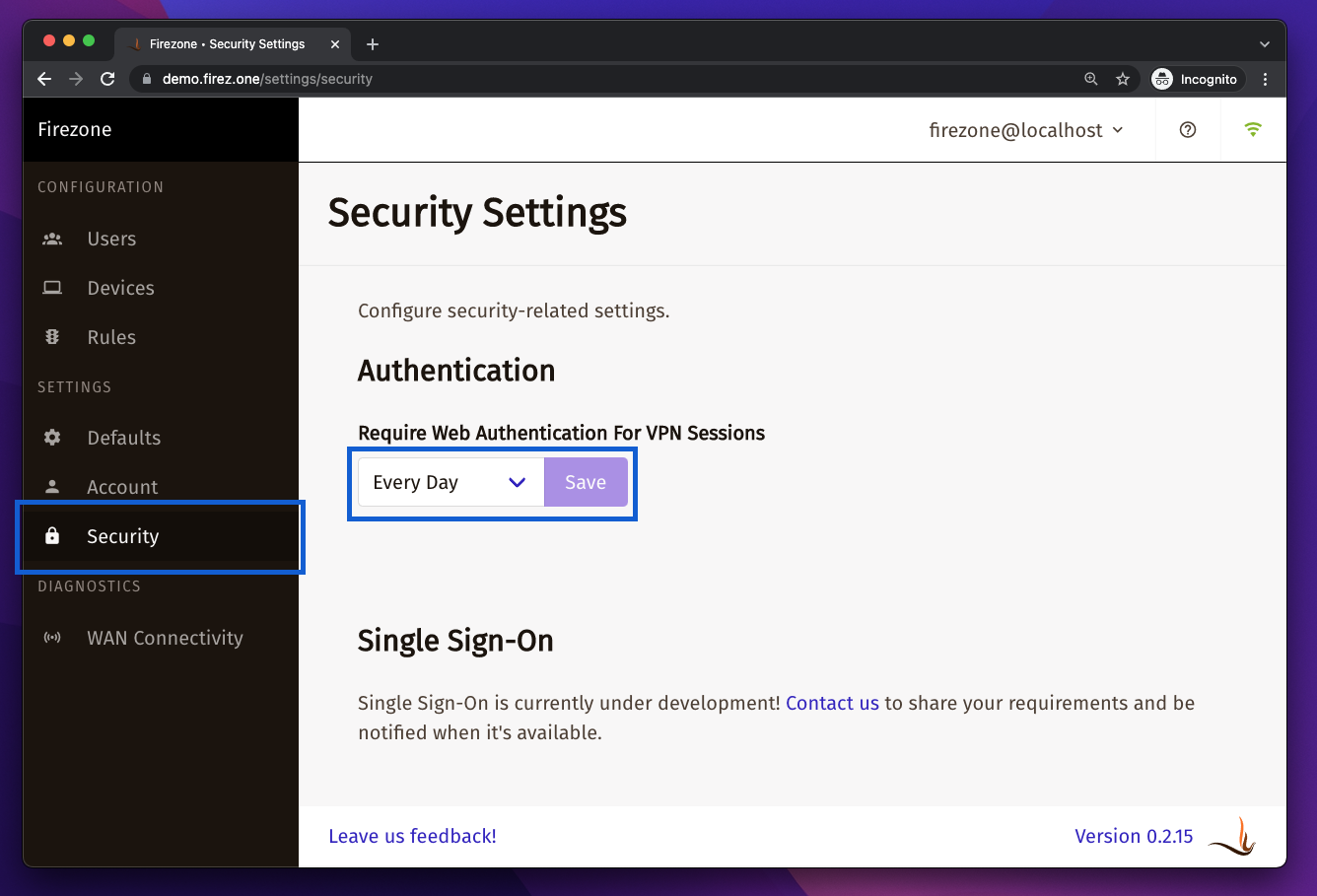
Periodic re-authentication can be enforced by changing the setting in `settings/security`.
|
||||
To re-authenticate a VPN session, a user will need to turn off their
|
||||
VPN session and log in to the Firezone portal (URL specified during
|
||||
Periodic re-authentication can be enforced by changing the setting in
|
||||
`settings/security`. This can be used to ensure a user must sign in to Firezone
|
||||
periodically in order to maintain their VPN session.
|
||||
|
||||
You can set the session length to a minimum of 1 hour and maximum of 90 days.
|
||||
Setting this to Never disables this setting, allowing VPN sessions indefinitely.
|
||||
This is the default.
|
||||
|
||||
To re-authenticate an expired VPN session, a user will need to turn off their
|
||||
VPN session and sign in to the Firezone portal (URL specified during
|
||||
[deployment]({%link docs/deploy/prerequisites.md%})
|
||||
).
|
||||
|
||||
|
||||
@@ -1,6 +1,6 @@
|
||||
---
|
||||
layout: default
|
||||
title: Local Email / Password
|
||||
title: Local Email / Password Authentication
|
||||
nav_order: 10
|
||||
parent: Authenticate
|
||||
description: >
|
||||
@@ -9,10 +9,8 @@ description: >
|
||||
---
|
||||
---
|
||||
|
||||
Firezone will use the user's email address and password
|
||||
to authenticate their VPN session.
|
||||
You can set the session length to a minimum of 1 hour and maximum of 90 days.
|
||||
Setting this to Never disables this setting, allowing VPN sessions indefinitely.
|
||||
This is the default.
|
||||
By default, Firezone will use local email / password for authenticating users to
|
||||
the Firezone portal. Administrators can add users and assign their passwords on
|
||||
`/users` page.
|
||||
|
||||
{:width="600"}
|
||||
|
||||
@@ -12,7 +12,7 @@ description: >
|
||||
Firezone can be deployed on most popular Linux distributions in a few minutes.
|
||||
Start by checking if your environment is listed on
|
||||
[supported platforms]({% link docs/deploy/supported-platforms.md %}).
|
||||
A kernel upgrade may be required to ensure WireGuard is supported.
|
||||
A kernel upgrade may be required to ensure WireGuard® is available.
|
||||
|
||||
\
|
||||
[Start Here: Supported Platforms]({%link docs/deploy/supported-platforms.md%}){:.btn.btn-purple}
|
||||
|
||||
@@ -72,7 +72,7 @@ If the Automatic Install fails, try these steps to install Firezone manually.
|
||||
`sudo firezone-ctl reconfigure`.
|
||||
1. Finally, create an admin user with `sudo firezone-ctl create-or-reset-admin`.
|
||||
The login credentials will be printed to the console output.
|
||||
1. Now you should be able to log into the web UI at the FQDN you specified in
|
||||
1. Now you should be able to sign in to the web UI at the FQDN you specified in
|
||||
step 5 above, e.g. `https://firezone.example.com`
|
||||
|
||||
Find solutions to common issues during deployment in [Troubleshoot]({%link docs/administer/troubleshoot.md%}).
|
||||
|
||||
@@ -5,7 +5,8 @@ nav_order: 1
|
||||
parent: Deploy
|
||||
description: >
|
||||
This section describes the supported platforms for Firezone. For
|
||||
some platforms a kernel upgrade may be required to ensure WireGuard is supported.
|
||||
some platforms a kernel upgrade may be required to ensure WireGuard® is
|
||||
available.
|
||||
---
|
||||
---
|
||||
|
||||
|
||||
@@ -9,7 +9,7 @@ description: >
|
||||
---
|
||||
|
||||
**We recommend asking users to generate their own device configs so the private
|
||||
key is only exposed to them.** Users can follow instructions on the
|
||||
key is exposed only to them.** Users can follow instructions on the
|
||||
[Client Instructions]({%link docs/user-guides/client-instructions.md%})
|
||||
page to generate their own device configs.
|
||||
|
||||
|
||||
@@ -71,7 +71,7 @@ the Firezone portal will prompt you to authenticate via that provider.
|
||||
|
||||
### Step 2 - Re-authenticate
|
||||
|
||||
Visit the URL of your Firezone portal and log in using credentials provided by your
|
||||
Visit the URL of your Firezone portal and sign in using credentials provided by your
|
||||
network admin.
|
||||
|
||||
{:width="600"}
|
||||
|
||||
@@ -1,20 +1,30 @@
|
||||
---
|
||||
layout: default
|
||||
title: IP Whitelisting via VPN
|
||||
title: Using Firezone as a NAT Gateway
|
||||
nav_order: 6
|
||||
parent: User Guides
|
||||
description: >
|
||||
Configure a VPN server with a static IP address to simplify
|
||||
IP whitelist management and add additional security.
|
||||
Configure a VPN server with a static IP address to act as
|
||||
a NAT gateway.
|
||||
---
|
||||
---
|
||||
|
||||
Firezone can be used as NAT gateway in order to provide a single,
|
||||
static egress IP for all of your team's traffic to flow out of.
|
||||
This is commonly used in the following scenarios:
|
||||
|
||||
* Consulting engagements: Ask your client to whitelist a single static
|
||||
IP address associated with your engagement instead of your employees'
|
||||
individual device IPs.
|
||||
* Masking your device IP or proxying your source IP for privacy or
|
||||
security reasons.
|
||||
|
||||
This guide will walk through a simple example restricting access for a
|
||||
self-hosted web app to a single whitelisted static IP running Firezone.
|
||||
In this example the protected resource and Firezone are
|
||||
in separate VPC regions.
|
||||
|
||||
This arrangement is commonly done in place of maintaining a whitelist for
|
||||
This arrangement is commonly done in place of maintaining an IP whitelist for
|
||||
multiple end users, which may become labor intensive to manage as the access
|
||||
list grows.
|
||||
|
||||
|
||||
@@ -80,12 +80,12 @@ default['firezone']['sysvinit_id'] = 'SUP'
|
||||
# For more information, see https://docs.firez.one/docs/user-guides/authentication/
|
||||
#
|
||||
# When local email/password authentication is used, users must be created by an Administrator
|
||||
# before they can log in.
|
||||
# before they can sign in.
|
||||
#
|
||||
# When SSO authentication methods are used, users are automatically added to Firezone
|
||||
# when logging in for the first time via the SSO provider.
|
||||
#
|
||||
# Users are uniquely identified by their email address, and may log in via multiple providers
|
||||
# Users are uniquely identified by their email address, and may sign in via multiple providers
|
||||
# if configured.
|
||||
|
||||
# Local email/password authentication is enabled by default
|
||||
|
||||
@@ -33,7 +33,7 @@ log 'admin_created' do
|
||||
|
||||
Firezone user created! Save this information because it will NOT be shown again.
|
||||
|
||||
Use this to log into the Web UI.
|
||||
Use this to sign in to the Web UI.
|
||||
|
||||
Email: #{node['firezone']['admin_email']}
|
||||
Password: #{node['firezone']['default_admin_password']}
|
||||
|
||||
Reference in New Issue
Block a user