mirror of
https://github.com/outbackdingo/firezone.git
synced 2026-01-27 10:18:54 +00:00
Add onelogin and okta SAML docs (#1108)
* add onelogin doc * add okta doc * add okta and onelogin to main README * wording and grammar * remove SLO for now * lint and table formatting * trailing whitespace * Update docs/docs/authenticate/saml/okta.mdx Co-authored-by: Jamil <jamilbk@users.noreply.github.com> Signed-off-by: Jason G <jason@firez.one> * Apply suggestions from code review Co-authored-by: Jamil <jamilbk@users.noreply.github.com> Signed-off-by: Jason G <jason@firez.one> * move provider support to top Signed-off-by: Jason G <jason@firez.one> Co-authored-by: Jamil <jamilbk@users.noreply.github.com>
This commit is contained in:
@@ -1,5 +1,5 @@
|
||||
---
|
||||
title: Onelogin
|
||||
title: OneLogin
|
||||
sidebar_position: 6
|
||||
---
|
||||
|
||||
@@ -8,7 +8,7 @@ through the generic OIDC connector. This guide will walk you through how to
|
||||
obtain the following config settings required for the integration:
|
||||
|
||||
1. **Config ID**: The provider's config ID. (e.g. `onelogin`)
|
||||
1. **Label**: The button label text that shows up on your Firezone login screen. (e.g. `Onelogin`)
|
||||
1. **Label**: The button label text that shows up on your Firezone login screen. (e.g. `OneLogin`)
|
||||
1. **Scope**: [OIDC scopes](https://openid.net/specs/openid-connect-basic-1_0.html#Scopes)
|
||||
to obtain from your OIDC provider. This should be set to `openid email profile`
|
||||
to provide Firezone with the user's email in the returned claims.
|
||||
@@ -35,7 +35,7 @@ or
|
||||
1. **Redirect URI**: Add your Firezone `<EXTERNAL_URL> + /auth/oidc/<Config ID>/callback/`
|
||||
(e.g. `https://firezone.example.com/auth/oidc/onelogin/callback/`).
|
||||
|
||||

|
||||

|
||||
|
||||
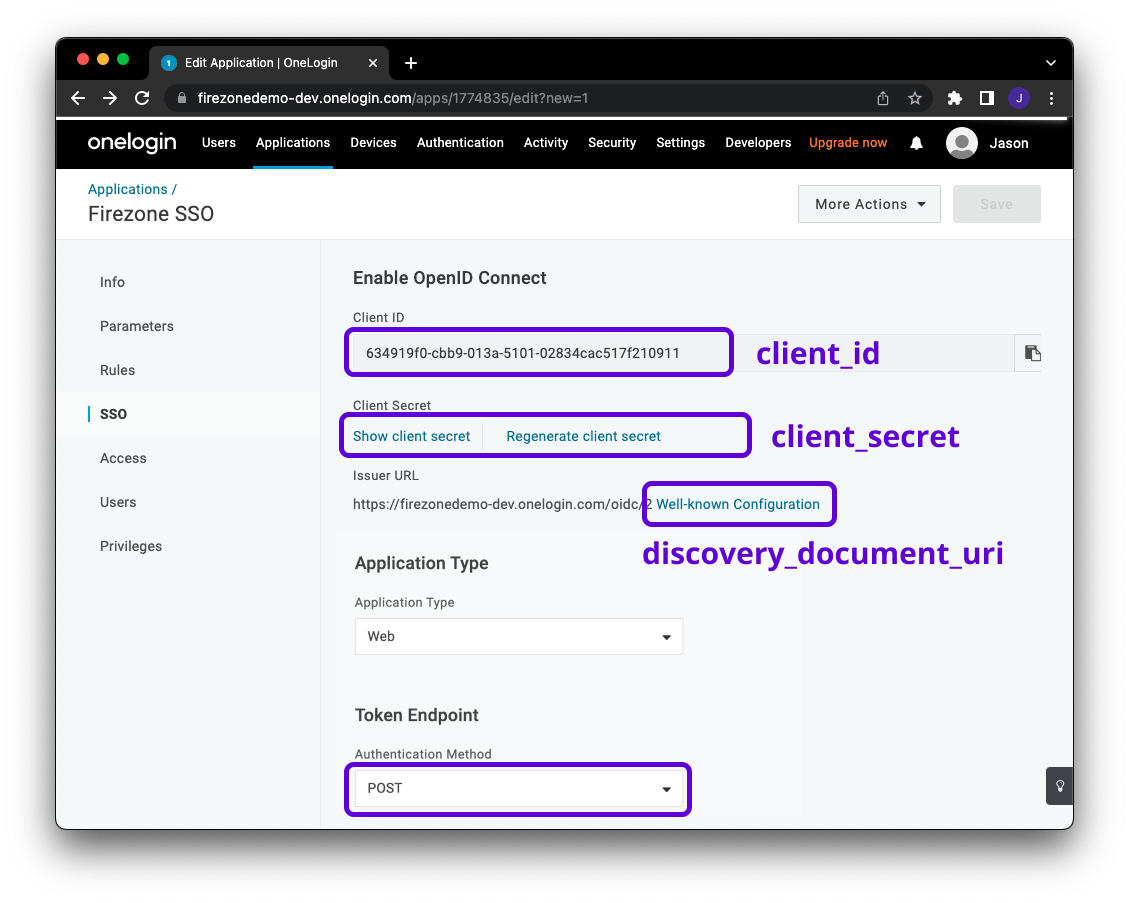
### Step 2 - Configure the OIDC Application
|
||||
|
||||
@@ -46,7 +46,7 @@ to **POST**.
|
||||
You will find the values for the config settings required by Firezone
|
||||
on this page as well.
|
||||
|
||||
|
||||

|
||||
|
||||
## Integrate With Firezone
|
||||
|
||||
@@ -58,4 +58,4 @@ Enable or disable the **Auto create users** option to automatically create
|
||||
an unprivileged user when signing in via this authentication mechanism.
|
||||
|
||||
And that's it! The configuration should be updated immediately.
|
||||
You should now see a `Sign in with Onelogin` button on the sign in page.
|
||||
You should now see a `Sign in with OneLogin` button on the sign in page.
|
||||
|
||||
@@ -10,11 +10,11 @@ Firezone supports Single Sign-On (SSO) via SAML 2.0.
|
||||
In general, most identity providers that support SAML 2.0 should work with
|
||||
Firezone.
|
||||
|
||||
<!-- TODO: Create SAML docs for popular providers -->
|
||||
<!-- 1. Okta -->
|
||||
<!-- 1. Onelogin -->
|
||||
<!-- 1. Azure AD -->
|
||||
<!-- 1. Google -->
|
||||
| Provider | Support Status | Notes |
|
||||
| --- | --- | --- |
|
||||
| [Okta](okta) | **Tested and supported** | |
|
||||
| [Onelogin](onelogin) | **Tested and supported** | |
|
||||
| Google Workspace | **[Known issues](https://github.com/firezone/firezone/issues/1049)** | |
|
||||
|
||||
Occasionally, providers that don't implement the full SAML 2.0 standard or use
|
||||
uncommon configurations may be problematic. If this is the case, [contact us](
|
||||
|
||||
48
docs/docs/authenticate/saml/okta.mdx
Normal file
48
docs/docs/authenticate/saml/okta.mdx
Normal file
@@ -0,0 +1,48 @@
|
||||
---
|
||||
title: Okta
|
||||
sidebar_position: 1
|
||||
description: Firezone's WireGuard®-based remote access platform supports using Okta as a single sign-on provider using a SAML 2.0 connector.
|
||||
---
|
||||
|
||||
:::note
|
||||
This guide assumes you have completed the prerequisite steps
|
||||
outlined [here](/authenticate/saml).
|
||||
:::
|
||||
|
||||
Firezone supports Single Sign-On (SSO) using Okta through the generic SAML 2.0 connector. This guide will walk you through how to configure the integration.
|
||||
|
||||
## Create a SAML connector
|
||||
|
||||
In the Okta admin portal, create a new app integration under
|
||||
the Application tab. Select `SAML 2.0` as the authentication method.
|
||||
Use the following config values during setup:
|
||||
|
||||
| Setting | Value |
|
||||
|--- |--- |
|
||||
| App name | `Firezone` |
|
||||
| App logo | [save link as](https://user-images.githubusercontent.com/52545545/155907625-a4f6c8c2-3952-488d-b244-3c37400846cf.png) |
|
||||
| Single sign on URL | `https://firezone.company.com/auth/saml/sp/consume/okta` |
|
||||
| Audience (EntityID) | `urn:firezone.dev:firezone-app` |
|
||||
| Name ID format | `EmailAddress` |
|
||||
| Application username | `Email` |
|
||||
| Update application username on | `Create and update` |
|
||||
|
||||
[Okta's documentation](https://help.okta.com/oie/en-us/Content/Topics/Apps/Apps_App_Integration_Wizard_SAML.htm)
|
||||
contains additional details on the purpose of each configuration setting. In all
|
||||
the fields above, replace `firezone.company.com` with your deployment's external URL.
|
||||
|
||||
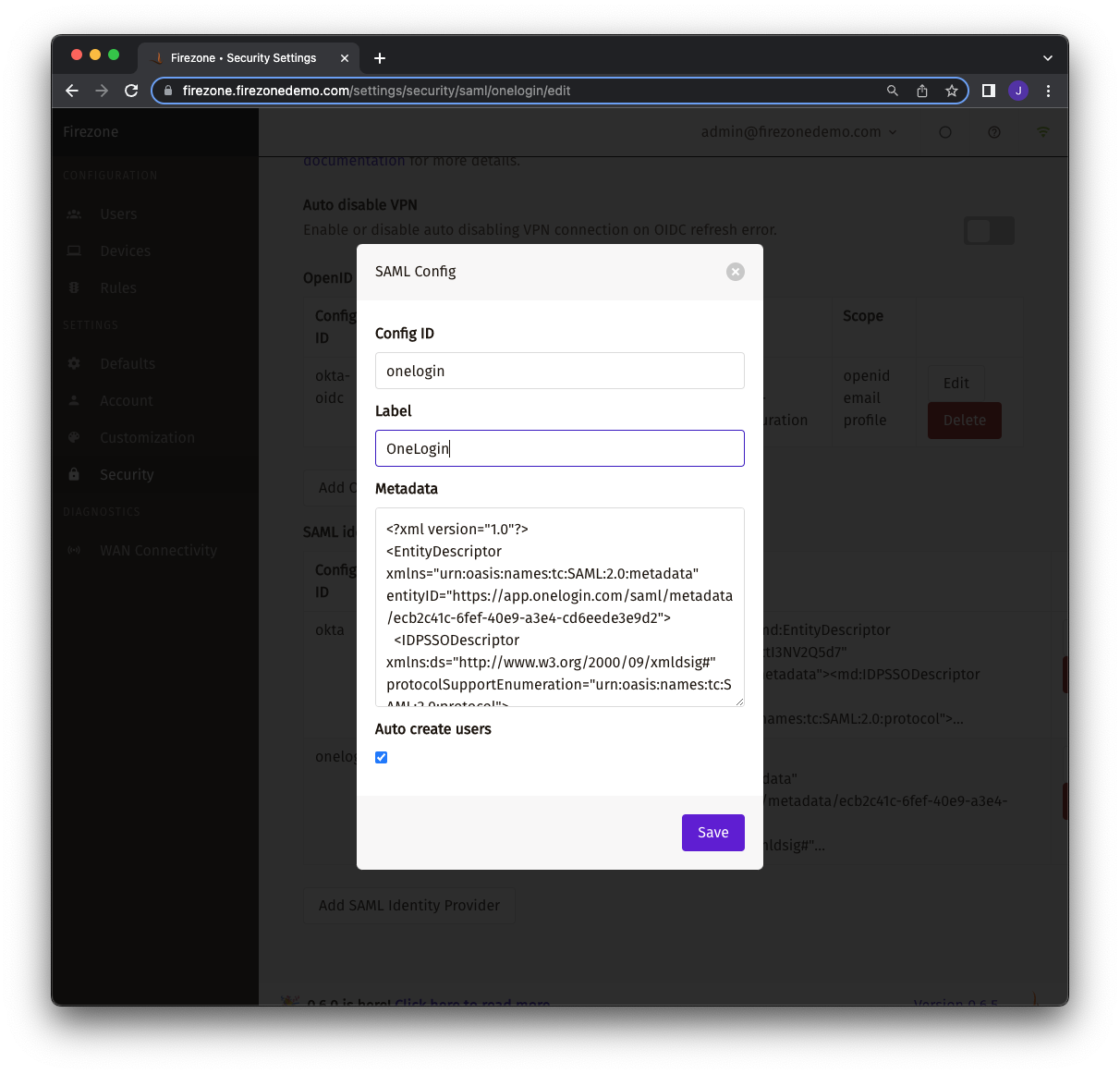
## Add SAML identity provider to Firezone
|
||||
|
||||
In the Firezone portal, add a SAML identity provider under the Security tab
|
||||
by filling out the following information:
|
||||
|
||||
| Setting | Value | Notes |
|
||||
|--- |--- |--- |
|
||||
| Config ID | `Okta` | Firezone uses this value to construct endpoints required in the SAML authentication flow (e.g., receiving assertions, login requests).|
|
||||
| Label | `Okta` | Appears on the sign in button for authentication. |
|
||||
| Metadata | see note | Upload the contents of the SAML metadata document you downloaded in the previous step from Okta. |
|
||||
|
||||
|
||||
|
||||
After saving the SAML config, you should see a `Sign in with Okta` button
|
||||
in your Firezone portal.
|
||||
53
docs/docs/authenticate/saml/onelogin.mdx
Normal file
53
docs/docs/authenticate/saml/onelogin.mdx
Normal file
@@ -0,0 +1,53 @@
|
||||
---
|
||||
title: OneLogin
|
||||
sidebar_position: 2
|
||||
description: Firezone's WireGuard based remote access platform supports using OneLogin as a single sign-on provider using a SAML 2.0 connector.
|
||||
---
|
||||
|
||||
:::note
|
||||
This guide assumes you have completed the prerequisite steps
|
||||
outlined [here](/authenticate/saml).
|
||||
:::
|
||||
|
||||
Firezone supports Single Sign-On (SSO) using OneLogin through the generic SAML 2.0 connector. This guide will walk you through how to configure the integration.
|
||||
|
||||
## Create a SAML connector
|
||||
|
||||
In the OneLogin admin portal, add an app under the application tab.
|
||||
Select `SAML Custom Connector (Advanced)` and provide the appropriate
|
||||
configuration settings under the under the configuration tab.
|
||||
|
||||
The following fields should be filled out on this page:
|
||||
|
||||
| Setting | Value |
|
||||
|--- |--- |
|
||||
| Audience (EntityID) | `urn:firezone.dev:firezone-app` |
|
||||
| Recipient | `https://firezone.company.com/auth/saml/sp/consume/onelogin` |
|
||||
| ACS URL Validator | `^https:\/\/firezone\.company\.com\/auth\/saml\/sp\/consume\/onelogin` |
|
||||
| ACS URL | `https://firezone.company.com/auth/saml/sp/consume/onelogin` |
|
||||
| Login URL | `https://firezone.company.com/auth/saml/auth/signin/onelogin` |
|
||||
| SAML initiator | `Service Provider` |
|
||||
| SAML signature element | `Both` |
|
||||
|
||||
[OneLogin's docs](https://onelogin.service-now.com/support?id=kb_article&sys_id=912bb23edbde7810fe39dde7489619de&kb_category=93e869b0db185340d5505eea4b961934)
|
||||
provide a good overview of each field's purpose. In all the fields above, replace `firezone.company.com`
|
||||
with your deployment's external URL.
|
||||
|
||||
Once complete, save the changes and download the SAML metadata document
|
||||
found unde the `More Actions` dropdown.
|
||||
|
||||
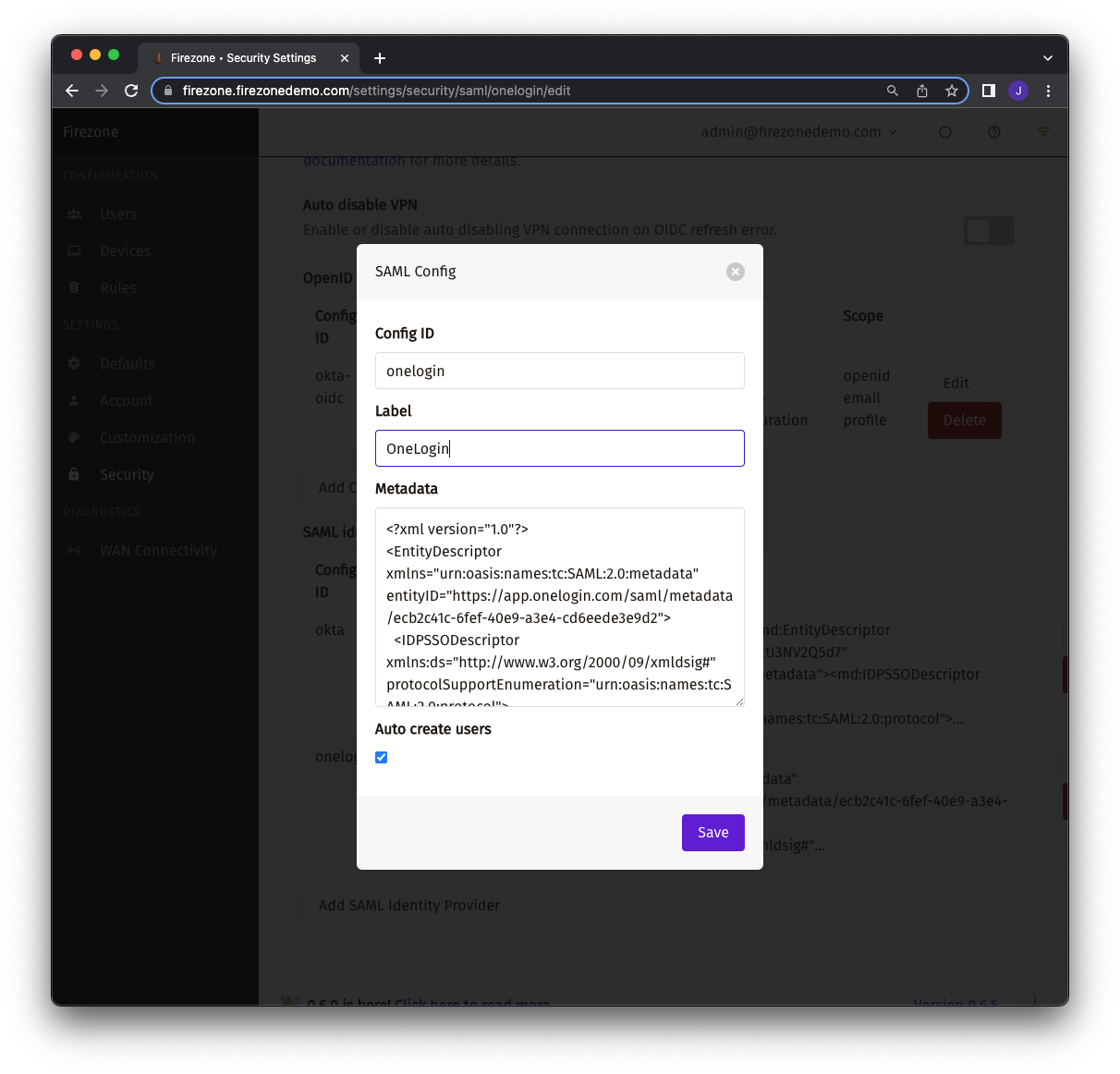
## Add SAML identity provider to Firezone
|
||||
|
||||
In the Firezone portal, add a SAML identity provider under the Security tab
|
||||
by filling out the following information:
|
||||
|
||||
| Setting | Value | Notes |
|
||||
|--- |--- |--- |
|
||||
| Config ID | `onelogin` | Firezone uses this value to construct endpoints required in the SAML authentication flow (e.g., receiving assertions, login requests).|
|
||||
| Label | `OneLogin` | Appears on the sign in button for authentication. |
|
||||
| Metadata | see note | Upload the contents of the SAML metadata document you downloaded in the previous step from OneLogin. |
|
||||
|
||||
|
||||
|
||||
After saving the SAML config, you should see a `Sign in with OneLogin` button
|
||||
in your Firezone portal.
|
||||
Reference in New Issue
Block a user