mirror of
https://github.com/outbackdingo/cozystack.git
synced 2026-01-29 18:19:00 +00:00
Compare commits
14 Commits
project-do
...
mariadb-op
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
0efd9ebc83 | ||
|
|
e17dcaa65e | ||
|
|
85d4ed251d | ||
|
|
f1c01a0fe8 | ||
|
|
2cff181279 | ||
|
|
2e3555600d | ||
|
|
98f488fcac | ||
|
|
1c6de1ccf5 | ||
|
|
235a2fcf47 | ||
|
|
24151b09f3 | ||
|
|
b37071f05e | ||
|
|
c64c6b549b | ||
|
|
df47d2f4a6 | ||
|
|
c0aea5a106 |
2
.gitignore
vendored
2
.gitignore
vendored
@@ -1 +1,3 @@
|
||||
_out
|
||||
.git
|
||||
.idea
|
||||
28
ADOPTERS.md
Normal file
28
ADOPTERS.md
Normal file
@@ -0,0 +1,28 @@
|
||||
# Adopters
|
||||
|
||||
Below you can find a list of organizations and users who have agreed to
|
||||
tell the world that they are using Cozystack in a production environment.
|
||||
|
||||
The goal of this list is to inspire others to do the same and to grow
|
||||
this open source community and project.
|
||||
|
||||
Please add your organization to this list. It takes 5 minutes of your time,
|
||||
but it means a lot to us.
|
||||
|
||||
## Updating this list
|
||||
|
||||
To add your organization to this list, you can either:
|
||||
|
||||
- [open a pull request](https://github.com/aenix-io/cozystack/pulls) to directly update this file, or
|
||||
- [edit this file](https://github.com/aenix-io/cozystack/blob/main/ADOPTERS.md) directly in GitHub
|
||||
|
||||
Feel free to ask in the Slack chat if you any questions and/or require
|
||||
assistance with updating this list.
|
||||
|
||||
## Cozystack Adopters
|
||||
|
||||
This list is sorted in chronological order, based on the submission date.
|
||||
|
||||
| Organization | Contact | Date | Description of Use |
|
||||
| ------------ | ------- | ---- | ------------------ |
|
||||
| [Ænix](https://aenix.io/) | @kvaps | 2024-02-14 | Ænix provides consulting services for cloud providers and uses Cozystack as the main tool for organizing managed services for them. |
|
||||
3
CODE_OF_CONDUCT.md
Normal file
3
CODE_OF_CONDUCT.md
Normal file
@@ -0,0 +1,3 @@
|
||||
# Code of Conduct
|
||||
|
||||
Cozystack follows the [CNCF Code of Conduct](https://github.com/cncf/foundation/blob/master/code-of-conduct.md).
|
||||
45
CONTRIBUTING.md
Normal file
45
CONTRIBUTING.md
Normal file
@@ -0,0 +1,45 @@
|
||||
# Contributing to Cozystack
|
||||
|
||||
Welcome! We are glad that you want to contribute to our Cozystack project! 💖
|
||||
|
||||
As you get started, you are in the best position to give us feedbacks on areas of our project that we need help with, including:
|
||||
|
||||
* Problems found while setting up the development environment
|
||||
* Gaps in our documentation
|
||||
* Bugs in our Github actions
|
||||
|
||||
First, though, it is important that you read the [code of conduct](CODE_OF_CONDUCT.md).
|
||||
|
||||
The guidelines below are a starting point. We don't want to limit your
|
||||
creativity, passion, and initiative. If you think there's a better way, please
|
||||
feel free to bring it up in a Github discussion, or open a pull request. We're
|
||||
certain there are always better ways to do things, we just need to start some
|
||||
constructive dialogue!
|
||||
|
||||
## Ways to contribute
|
||||
|
||||
We welcome many types of contributions including:
|
||||
|
||||
* New features
|
||||
* Builds, CI/CD
|
||||
* Bug fixes
|
||||
* [Documentation](https://github.com/aenix-io/cozystack-website/tree/main)
|
||||
* Issue Triage
|
||||
* Answering questions on Slack or Github Discussions
|
||||
* Web design
|
||||
* Communications / Social Media / Blog Posts
|
||||
* Events participation
|
||||
* Release management
|
||||
|
||||
## Ask for Help
|
||||
|
||||
The best way to reach us with a question when contributing is to drop a line in
|
||||
our [Telegram channel](https://t.me/cozystack), or start a new Github discussion.
|
||||
|
||||
## Raising Issues
|
||||
|
||||
When raising issues, please specify the following:
|
||||
|
||||
- A scenario where the issue occurred (with details on how to reproduce it)
|
||||
- Errors and log messages that are displayed by the involved software
|
||||
- Any other detail that might be useful
|
||||
7
MAINTAINERS.md
Normal file
7
MAINTAINERS.md
Normal file
@@ -0,0 +1,7 @@
|
||||
# The Cozystack Maintainers
|
||||
|
||||
| Maintainer | GitHub Username | Company |
|
||||
| ---------- | --------------- | ------- |
|
||||
| Andrei Kvapil | [@kvaps](https://github.com/kvaps) | Ænix |
|
||||
| George Gaál | [@gecube](https://github.com/gecube) | Ænix |
|
||||
| Eduard Generalov | [@egeneralov](https://github.com/egeneralov) | Ænix |
|
||||
553
README.md
553
README.md
@@ -10,7 +10,7 @@
|
||||
|
||||
# Cozystack
|
||||
|
||||
**Cozystack** is an open-source **PaaS platform** for cloud providers.
|
||||
**Cozystack** is a free PaaS platform and framework for building clouds.
|
||||
|
||||
With Cozystack, you can transform your bunch of servers into an intelligent system with a simple REST API for spawning Kubernetes clusters, Database-as-a-Service, virtual machines, load balancers, HTTP caching services, and other services with ease.
|
||||
|
||||
@@ -18,548 +18,55 @@ You can use Cozystack to build your own cloud or to provide a cost-effective dev
|
||||
|
||||
## Use-Cases
|
||||
|
||||
### As a backend for a public cloud
|
||||
* [**Using Cozystack to build public cloud**](https://cozystack.io/docs/use-cases/public-cloud/)
|
||||
You can use Cozystack as backend for a public cloud
|
||||
|
||||
Cozystack positions itself as a kind of framework for building public clouds. The key word here is framework. In this case, it's important to understand that Cozystack is made for cloud providers, not for end users.
|
||||
* [**Using Cozystack to build private cloud**](https://cozystack.io/docs/use-cases/private-cloud/)
|
||||
You can use Cozystack as platform to build a private cloud powered by Infrastructure-as-Code approach
|
||||
|
||||
Despite having a graphical interface, the current security model does not imply public user access to your management cluster.
|
||||
|
||||
Instead, end users get access to their own Kubernetes clusters, can order LoadBalancers and additional services from it, but they have no access and know nothing about your management cluster powered by Cozystack.
|
||||
|
||||
Thus, to integrate with your billing system, it's enough to teach your system to go to the management Kubernetes and place a YAML file signifying the service you're interested in. Cozystack will do the rest of the work for you.
|
||||
|
||||
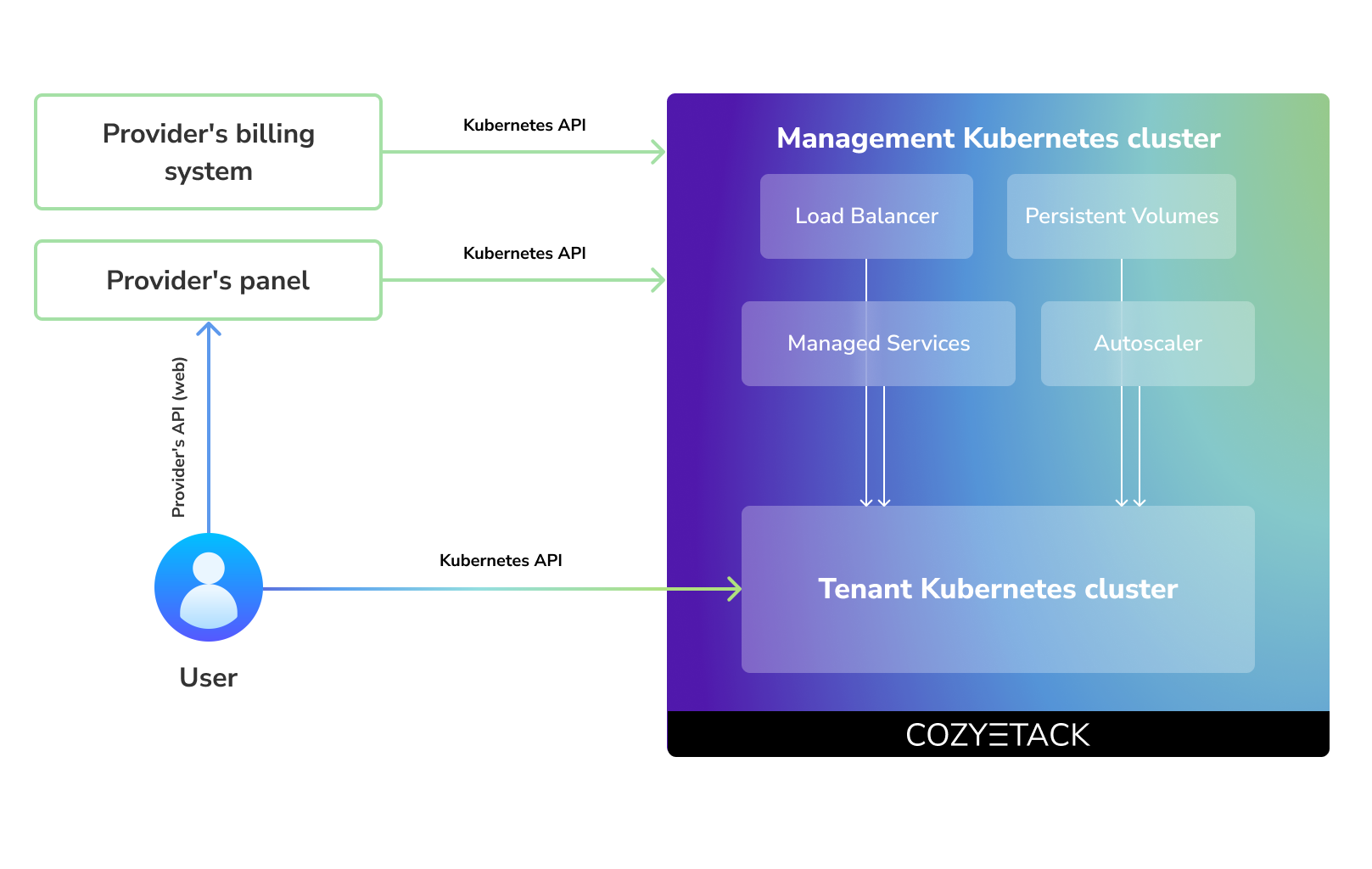
|
||||
|
||||
### As a private cloud for Infrastructure-as-Code
|
||||
|
||||
One of the use cases is a self-portal for users within your company, where they can order the service they're interested in or a managed database.
|
||||
|
||||
You can implement best GitOps practices, where users will launch their own Kubernetes clusters and databases for their needs with a simple commit of configuration into your infrastructure Git repository.
|
||||
|
||||
Thanks to the standardization of the approach to deploying applications, you can expand the platform's capabilities using the functionality of standard Helm charts.
|
||||
|
||||
### As a Kubernetes distribution for Bare Metal
|
||||
|
||||
We created Cozystack primarily for our own needs, having vast experience in building reliable systems on bare metal infrastructure. This experience led to the formation of a separate boxed product, which is aimed at standardizing and providing a ready-to-use tool for managing your infrastructure.
|
||||
|
||||
Currently, Cozystack already solves a huge scope of infrastructure tasks: starting from provisioning bare metal servers, having a ready monitoring system, fast and reliable storage, a network fabric with the possibility of interconnect with your infrastructure, the ability to run virtual machines, databases, and much more right out of the box.
|
||||
|
||||
All this makes Cozystack a convenient platform for delivering and launching your application on Bare Metal.
|
||||
* [**Using Cozystack as Kubernetes distribution**](https://cozystack.io/docs/use-cases/kubernetes-distribution/)
|
||||
You can use Cozystack as Kubernetes distribution for Bare Metal
|
||||
|
||||
## Screenshot
|
||||
|
||||
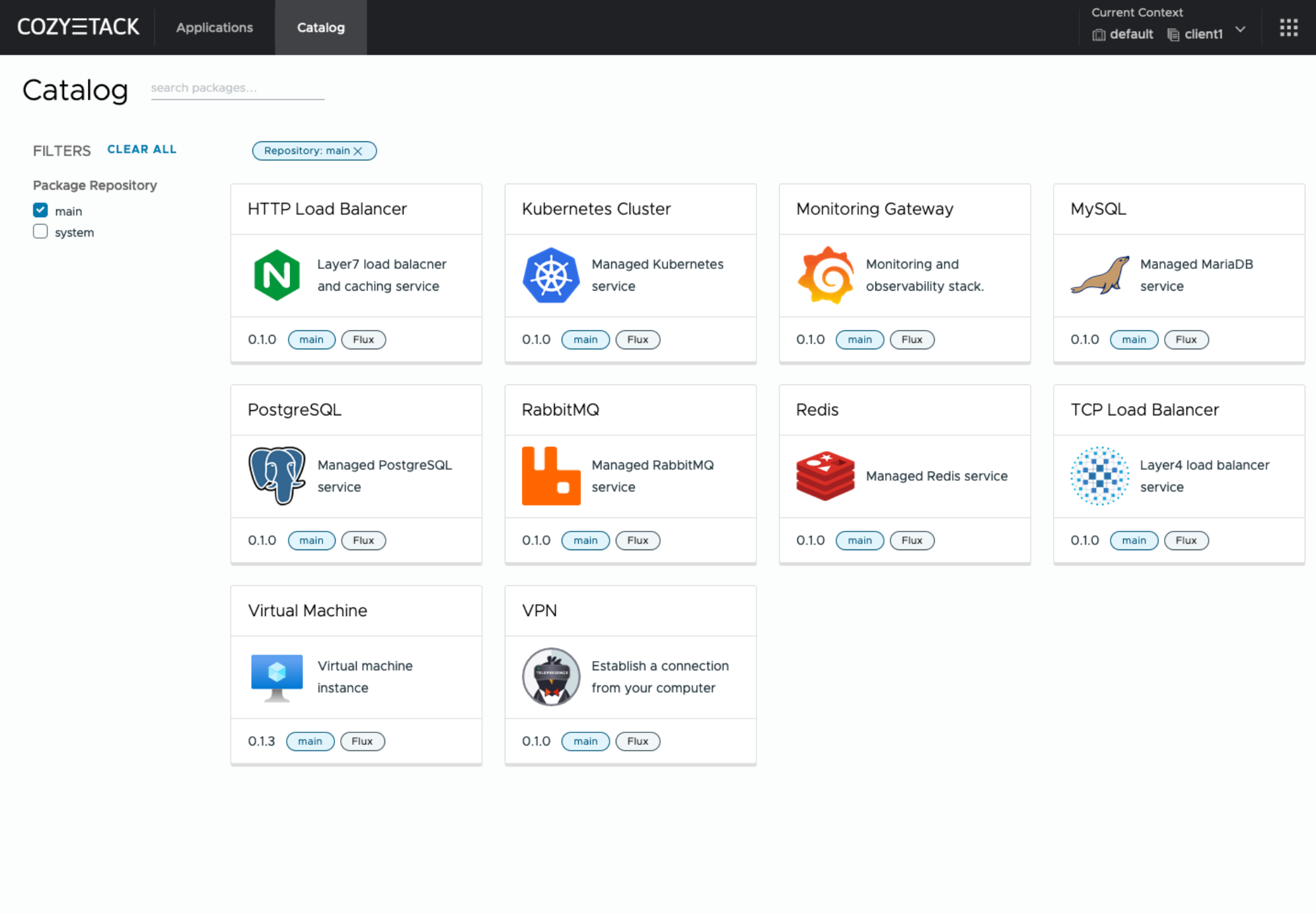
|
||||
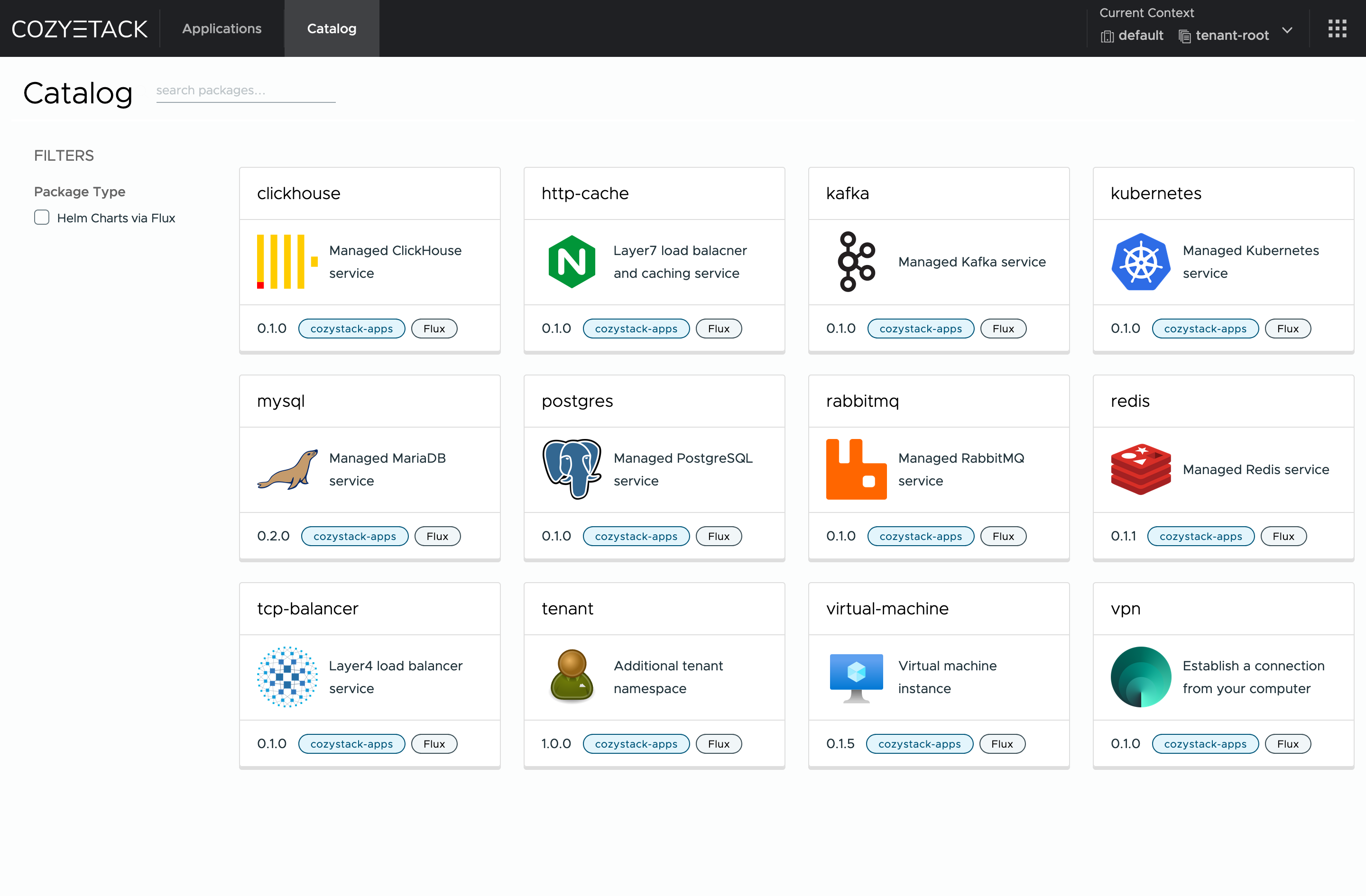
|
||||
|
||||
## Core values
|
||||
## Documentation
|
||||
|
||||
### Standardization and unification
|
||||
All components of the platform are based on open source tools and technologies which are widely known in the industry.
|
||||
The documentation is located on official [cozystack.io](cozystack.io) website.
|
||||
|
||||
### Collaborate, not compete
|
||||
If a feature being developed for the platform could be useful to a upstream project, it should be contributed to upstream project, rather than being implemented within the platform.
|
||||
Read [Get Started](https://cozystack.io/docs/get-started/) section for a quick start.
|
||||
|
||||
### API-first
|
||||
Cozystack is based on Kubernetes and involves close interaction with its API. We don't aim to completely hide the all elements behind a pretty UI or any sort of customizations; instead, we provide a standard interface and teach users how to work with basic primitives. The web interface is used solely for deploying applications and quickly diving into basic concepts of platform.
|
||||
If you encounter any difficulties, start with the [troubleshooting guide](https://cozystack.io/docs/troubleshooting/), and work your way through the process that we've outlined.
|
||||
|
||||
## Quick Start
|
||||
## Versioning
|
||||
|
||||
### Prepare infrastructure
|
||||
Versioning adheres to the [Semantic Versioning](http://semver.org/) principles.
|
||||
A full list of the available releases is available in the GitHub repository's [Release](https://github.com/aenix-io/cozystack/releases) section.
|
||||
|
||||
- [Roadmap](https://github.com/orgs/aenix-io/projects/2)
|
||||
|
||||
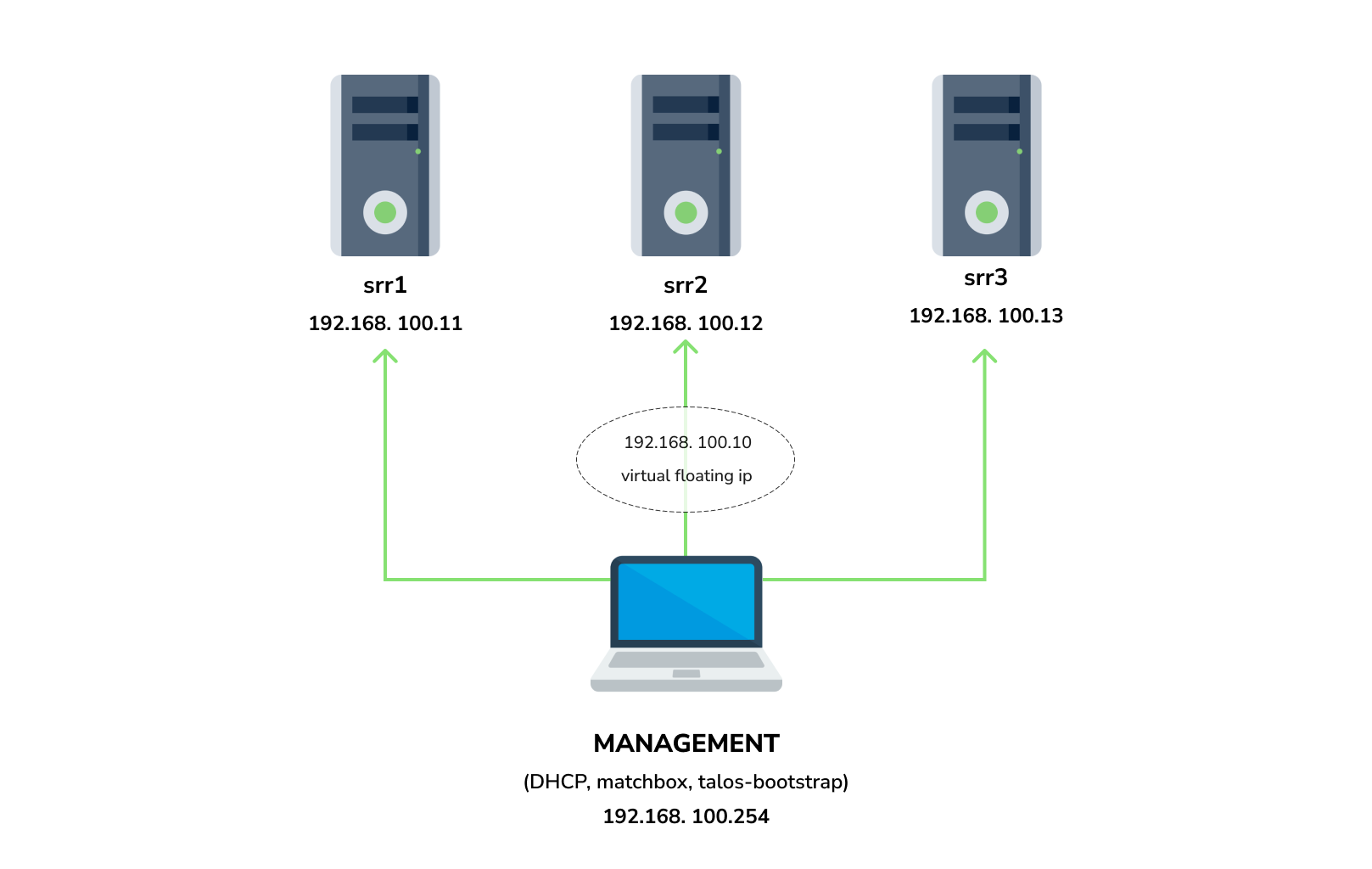
|
||||
## Contributions
|
||||
|
||||
You need 3 physical servers or VMs with nested virtualisation:
|
||||
Contributions are highly appreciated and very welcomed!
|
||||
|
||||
```
|
||||
CPU: 4 cores
|
||||
CPU model: host
|
||||
RAM: 8-16 GB
|
||||
HDD1: 32 GB
|
||||
HDD2: 100GB (raw)
|
||||
```
|
||||
In case of bugs, please, check if the issue has been already opened by checking the [GitHub Issues](https://github.com/aenix-io/cozystack/issues) section.
|
||||
In case it isn't, you can open a new one: a detailed report will help us to replicate it, assess it, and work on a fix.
|
||||
|
||||
And one management VM or physical server connected to the same network.
|
||||
Any Linux system installed on it (eg. Ubuntu should be enough)
|
||||
You can express your intention in working on the fix on your own.
|
||||
Commits are used to generate the changelog, and their author will be referenced in it.
|
||||
|
||||
**Note:** The VM should support `x86-64-v2` architecture, the most probably you can achieve this by setting cpu model to `host`
|
||||
In case of **Feature Requests** please use the [Discussion's Feature Request section](https://github.com/aenix-io/cozystack/discussions/categories/feature-requests).
|
||||
|
||||
#### Install dependencies:
|
||||
## License
|
||||
|
||||
- `docker`
|
||||
- `talosctl`
|
||||
- `dialog`
|
||||
- `nmap`
|
||||
- `make`
|
||||
- `yq`
|
||||
- `kubectl`
|
||||
- `helm`
|
||||
Cozystack is licensed under Apache 2.0.
|
||||
The code is provided as-is with no warranties.
|
||||
|
||||
### Netboot server
|
||||
## Commercial Support
|
||||
|
||||
Start matchbox with prebuilt Talos image for Cozystack:
|
||||
[**Ænix**](https://aenix.io) offers enterprise-grade support, available 24/7.
|
||||
|
||||
```bash
|
||||
sudo docker run --name=matchbox -d --net=host ghcr.io/aenix-io/cozystack/matchbox:v0.0.2 \
|
||||
-address=:8080 \
|
||||
-log-level=debug
|
||||
```
|
||||
We provide all types of assistance, including consultations, development of missing features, design, assistance with installation, and integration.
|
||||
|
||||
Start DHCP-Server:
|
||||
```bash
|
||||
sudo docker run --name=dnsmasq -d --cap-add=NET_ADMIN --net=host quay.io/poseidon/dnsmasq \
|
||||
-d -q -p0 \
|
||||
--dhcp-range=192.168.100.3,192.168.100.254 \
|
||||
--dhcp-option=option:router,192.168.100.1 \
|
||||
--enable-tftp \
|
||||
--tftp-root=/var/lib/tftpboot \
|
||||
--dhcp-match=set:bios,option:client-arch,0 \
|
||||
--dhcp-boot=tag:bios,undionly.kpxe \
|
||||
--dhcp-match=set:efi32,option:client-arch,6 \
|
||||
--dhcp-boot=tag:efi32,ipxe.efi \
|
||||
--dhcp-match=set:efibc,option:client-arch,7 \
|
||||
--dhcp-boot=tag:efibc,ipxe.efi \
|
||||
--dhcp-match=set:efi64,option:client-arch,9 \
|
||||
--dhcp-boot=tag:efi64,ipxe.efi \
|
||||
--dhcp-userclass=set:ipxe,iPXE \
|
||||
--dhcp-boot=tag:ipxe,http://192.168.100.254:8080/boot.ipxe \
|
||||
--log-queries \
|
||||
--log-dhcp
|
||||
```
|
||||
|
||||
Where:
|
||||
- `192.168.100.3,192.168.100.254` range to allocate IPs from
|
||||
- `192.168.100.1` your gateway
|
||||
- `192.168.100.254` is address of your management server
|
||||
|
||||
Check status of containers:
|
||||
|
||||
```
|
||||
docker ps
|
||||
```
|
||||
|
||||
example output:
|
||||
|
||||
```console
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
22044f26f74d quay.io/poseidon/dnsmasq "/usr/sbin/dnsmasq -…" 6 seconds ago Up 5 seconds dnsmasq
|
||||
231ad81ff9e0 ghcr.io/aenix-io/cozystack/matchbox:v0.0.2 "/matchbox -address=…" 58 seconds ago Up 57 seconds matchbox
|
||||
```
|
||||
|
||||
### Bootstrap cluster
|
||||
|
||||
Write configuration for Cozystack:
|
||||
|
||||
```yaml
|
||||
cat > patch.yaml <<\EOT
|
||||
machine:
|
||||
kubelet:
|
||||
nodeIP:
|
||||
validSubnets:
|
||||
- 192.168.100.0/24
|
||||
kernel:
|
||||
modules:
|
||||
- name: openvswitch
|
||||
- name: drbd
|
||||
parameters:
|
||||
- usermode_helper=disabled
|
||||
- name: zfs
|
||||
install:
|
||||
image: ghcr.io/aenix-io/cozystack/talos:v1.6.4
|
||||
files:
|
||||
- content: |
|
||||
[plugins]
|
||||
[plugins."io.containerd.grpc.v1.cri"]
|
||||
device_ownership_from_security_context = true
|
||||
path: /etc/cri/conf.d/20-customization.part
|
||||
op: create
|
||||
|
||||
cluster:
|
||||
network:
|
||||
cni:
|
||||
name: none
|
||||
podSubnets:
|
||||
- 10.244.0.0/16
|
||||
serviceSubnets:
|
||||
- 10.96.0.0/16
|
||||
EOT
|
||||
|
||||
cat > patch-controlplane.yaml <<\EOT
|
||||
cluster:
|
||||
allowSchedulingOnControlPlanes: true
|
||||
controllerManager:
|
||||
extraArgs:
|
||||
bind-address: 0.0.0.0
|
||||
scheduler:
|
||||
extraArgs:
|
||||
bind-address: 0.0.0.0
|
||||
apiServer:
|
||||
certSANs:
|
||||
- 127.0.0.1
|
||||
proxy:
|
||||
disabled: true
|
||||
discovery:
|
||||
enabled: false
|
||||
etcd:
|
||||
advertisedSubnets:
|
||||
- 192.168.100.0/24
|
||||
EOT
|
||||
```
|
||||
|
||||
Run [talos-bootstrap](https://github.com/aenix-io/talos-bootstrap/) to deploy cluster:
|
||||
|
||||
```bash
|
||||
talos-bootstrap install
|
||||
```
|
||||
|
||||
Save admin kubeconfig to access your Kubernetes cluster:
|
||||
```bash
|
||||
cp -i kubeconfig ~/.kube/config
|
||||
```
|
||||
|
||||
Check connection:
|
||||
```bash
|
||||
kubectl get ns
|
||||
```
|
||||
|
||||
example output:
|
||||
```console
|
||||
NAME STATUS AGE
|
||||
default Active 7m56s
|
||||
kube-node-lease Active 7m56s
|
||||
kube-public Active 7m56s
|
||||
kube-system Active 7m56s
|
||||
```
|
||||
|
||||
|
||||
**Note:**: All nodes should currently show as "Not Ready", don't worry about that, this is because you disabled the default CNI plugin in the previous step. Cozystack will install it's own CNI-plugin on the next step.
|
||||
|
||||
|
||||
### Install Cozystack
|
||||
|
||||
|
||||
write config for cozystack:
|
||||
|
||||
**Note:** please make sure that you written the same setting specified in `patch.yaml` and `patch-controlplane.yaml` files.
|
||||
|
||||
```yaml
|
||||
cat > cozystack-config.yaml <<\EOT
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: cozystack
|
||||
namespace: cozy-system
|
||||
data:
|
||||
cluster-name: "cozystack"
|
||||
ipv4-pod-cidr: "10.244.0.0/16"
|
||||
ipv4-pod-gateway: "10.244.0.1"
|
||||
ipv4-svc-cidr: "10.96.0.0/16"
|
||||
ipv4-join-cidr: "100.64.0.0/16"
|
||||
EOT
|
||||
```
|
||||
|
||||
Create namesapce and install Cozystack system components:
|
||||
|
||||
```bash
|
||||
kubectl create ns cozy-system
|
||||
kubectl apply -f cozystack-config.yaml
|
||||
kubectl apply -f manifests/cozystack-installer.yaml
|
||||
```
|
||||
|
||||
(optional) You can track the logs of installer:
|
||||
```bash
|
||||
kubectl logs -n cozy-system deploy/cozystack -f
|
||||
```
|
||||
|
||||
Wait for a while, then check the status of installation:
|
||||
```bash
|
||||
kubectl get hr -A
|
||||
```
|
||||
|
||||
Wait until all releases become to `Ready` state:
|
||||
```console
|
||||
NAMESPACE NAME AGE READY STATUS
|
||||
cozy-cert-manager cert-manager 4m1s True Release reconciliation succeeded
|
||||
cozy-cert-manager cert-manager-issuers 4m1s True Release reconciliation succeeded
|
||||
cozy-cilium cilium 4m1s True Release reconciliation succeeded
|
||||
cozy-cluster-api capi-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-cluster-api capi-providers 4m1s True Release reconciliation succeeded
|
||||
cozy-dashboard dashboard 4m1s True Release reconciliation succeeded
|
||||
cozy-fluxcd cozy-fluxcd 4m1s True Release reconciliation succeeded
|
||||
cozy-grafana-operator grafana-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-kamaji kamaji 4m1s True Release reconciliation succeeded
|
||||
cozy-kubeovn kubeovn 4m1s True Release reconciliation succeeded
|
||||
cozy-kubevirt-cdi kubevirt-cdi 4m1s True Release reconciliation succeeded
|
||||
cozy-kubevirt-cdi kubevirt-cdi-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-kubevirt kubevirt 4m1s True Release reconciliation succeeded
|
||||
cozy-kubevirt kubevirt-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-linstor linstor 4m1s True Release reconciliation succeeded
|
||||
cozy-linstor piraeus-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-mariadb-operator mariadb-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-metallb metallb 4m1s True Release reconciliation succeeded
|
||||
cozy-monitoring monitoring 4m1s True Release reconciliation succeeded
|
||||
cozy-postgres-operator postgres-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-rabbitmq-operator rabbitmq-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-redis-operator redis-operator 4m1s True Release reconciliation succeeded
|
||||
cozy-telepresence telepresence 4m1s True Release reconciliation succeeded
|
||||
cozy-victoria-metrics-operator victoria-metrics-operator 4m1s True Release reconciliation succeeded
|
||||
tenant-root tenant-root 4m1s True Release reconciliation succeeded
|
||||
```
|
||||
|
||||
#### Configure Storage
|
||||
|
||||
Setup alias to access LINSTOR:
|
||||
```bash
|
||||
alias linstor='kubectl exec -n cozy-linstor deploy/linstor-controller -- linstor'
|
||||
```
|
||||
|
||||
list your nodes
|
||||
```bash
|
||||
linstor node list
|
||||
```
|
||||
|
||||
example output:
|
||||
|
||||
```console
|
||||
+-------------------------------------------------------+
|
||||
| Node | NodeType | Addresses | State |
|
||||
|=======================================================|
|
||||
| srv1 | SATELLITE | 192.168.100.11:3367 (SSL) | Online |
|
||||
| srv2 | SATELLITE | 192.168.100.12:3367 (SSL) | Online |
|
||||
| srv3 | SATELLITE | 192.168.100.13:3367 (SSL) | Online |
|
||||
+-------------------------------------------------------+
|
||||
```
|
||||
|
||||
list empty devices:
|
||||
|
||||
```bash
|
||||
linstor physical-storage list
|
||||
```
|
||||
|
||||
example output:
|
||||
```console
|
||||
+--------------------------------------------+
|
||||
| Size | Rotational | Nodes |
|
||||
|============================================|
|
||||
| 107374182400 | True | srv3[/dev/sdb] |
|
||||
| | | srv1[/dev/sdb] |
|
||||
| | | srv2[/dev/sdb] |
|
||||
+--------------------------------------------+
|
||||
```
|
||||
|
||||
|
||||
create storage pools:
|
||||
|
||||
```bash
|
||||
linstor ps cdp lvm srv1 /dev/sdb --pool-name data --storage-pool data
|
||||
linstor ps cdp lvm srv2 /dev/sdb --pool-name data --storage-pool data
|
||||
linstor ps cdp lvm srv3 /dev/sdb --pool-name data --storage-pool data
|
||||
```
|
||||
|
||||
list storage pools:
|
||||
|
||||
```bash
|
||||
linstor sp l
|
||||
```
|
||||
|
||||
example output:
|
||||
|
||||
```console
|
||||
+-------------------------------------------------------------------------------------------------------------------------------------+
|
||||
| StoragePool | Node | Driver | PoolName | FreeCapacity | TotalCapacity | CanSnapshots | State | SharedName |
|
||||
|=====================================================================================================================================|
|
||||
| DfltDisklessStorPool | srv1 | DISKLESS | | | | False | Ok | srv1;DfltDisklessStorPool |
|
||||
| DfltDisklessStorPool | srv2 | DISKLESS | | | | False | Ok | srv2;DfltDisklessStorPool |
|
||||
| DfltDisklessStorPool | srv3 | DISKLESS | | | | False | Ok | srv3;DfltDisklessStorPool |
|
||||
| data | srv1 | LVM | data | 100.00 GiB | 100.00 GiB | False | Ok | srv1;data |
|
||||
| data | srv2 | LVM | data | 100.00 GiB | 100.00 GiB | False | Ok | srv2;data |
|
||||
| data | srv3 | LVM | data | 100.00 GiB | 100.00 GiB | False | Ok | srv3;data |
|
||||
+-------------------------------------------------------------------------------------------------------------------------------------+
|
||||
```
|
||||
|
||||
|
||||
Create default storage classes:
|
||||
```yaml
|
||||
kubectl create -f- <<EOT
|
||||
---
|
||||
apiVersion: storage.k8s.io/v1
|
||||
kind: StorageClass
|
||||
metadata:
|
||||
name: local
|
||||
annotations:
|
||||
storageclass.kubernetes.io/is-default-class: "true"
|
||||
provisioner: linstor.csi.linbit.com
|
||||
parameters:
|
||||
linstor.csi.linbit.com/storagePool: "data"
|
||||
linstor.csi.linbit.com/layerList: "storage"
|
||||
linstor.csi.linbit.com/allowRemoteVolumeAccess: "false"
|
||||
volumeBindingMode: WaitForFirstConsumer
|
||||
allowVolumeExpansion: true
|
||||
---
|
||||
apiVersion: storage.k8s.io/v1
|
||||
kind: StorageClass
|
||||
metadata:
|
||||
name: replicated
|
||||
provisioner: linstor.csi.linbit.com
|
||||
parameters:
|
||||
linstor.csi.linbit.com/storagePool: "data"
|
||||
linstor.csi.linbit.com/autoPlace: "3"
|
||||
linstor.csi.linbit.com/layerList: "drbd storage"
|
||||
linstor.csi.linbit.com/allowRemoteVolumeAccess: "true"
|
||||
property.linstor.csi.linbit.com/DrbdOptions/auto-quorum: suspend-io
|
||||
property.linstor.csi.linbit.com/DrbdOptions/Resource/on-no-data-accessible: suspend-io
|
||||
property.linstor.csi.linbit.com/DrbdOptions/Resource/on-suspended-primary-outdated: force-secondary
|
||||
property.linstor.csi.linbit.com/DrbdOptions/Net/rr-conflict: retry-connect
|
||||
volumeBindingMode: WaitForFirstConsumer
|
||||
allowVolumeExpansion: true
|
||||
EOT
|
||||
```
|
||||
|
||||
list storageclasses:
|
||||
|
||||
```bash
|
||||
kubectl get storageclasses
|
||||
```
|
||||
|
||||
example output:
|
||||
```console
|
||||
NAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION AGE
|
||||
local (default) linstor.csi.linbit.com Delete WaitForFirstConsumer true 11m
|
||||
replicated linstor.csi.linbit.com Delete WaitForFirstConsumer true 11m
|
||||
```
|
||||
|
||||
#### Configure Networking interconnection
|
||||
|
||||
To access your services select the range of unused IPs, eg. `192.168.100.200-192.168.100.250`
|
||||
|
||||
**Note:** These IPs should be from the same network as nodes or they should have all necessary routes for them.
|
||||
|
||||
Configure MetalLB to use and announce this range:
|
||||
```yaml
|
||||
kubectl create -f- <<EOT
|
||||
---
|
||||
apiVersion: metallb.io/v1beta1
|
||||
kind: L2Advertisement
|
||||
metadata:
|
||||
name: cozystack
|
||||
namespace: cozy-metallb
|
||||
spec:
|
||||
ipAddressPools:
|
||||
- cozystack
|
||||
---
|
||||
apiVersion: metallb.io/v1beta1
|
||||
kind: IPAddressPool
|
||||
metadata:
|
||||
name: cozystack
|
||||
namespace: cozy-metallb
|
||||
spec:
|
||||
addresses:
|
||||
- 192.168.100.200-192.168.100.250
|
||||
autoAssign: true
|
||||
avoidBuggyIPs: false
|
||||
EOT
|
||||
```
|
||||
|
||||
#### Setup basic applications
|
||||
|
||||
Get token from `tenant-root`:
|
||||
```bash
|
||||
kubectl get secret -n tenant-root tenant-root -o go-template='{{ printf "%s\n" (index .data "token" | base64decode) }}'
|
||||
```
|
||||
|
||||
Enable port forward to cozy-dashboard:
|
||||
```bash
|
||||
kubectl port-forward -n cozy-dashboard svc/dashboard 8080:80
|
||||
```
|
||||
|
||||
Open: http://localhost:8080/
|
||||
|
||||
- Select `tenant-root`
|
||||
- Click `Upgrade` button
|
||||
- Write a domain into `host` which you wish to use as parent domain for all deployed applications
|
||||
**Note:**
|
||||
- if you have no domain yet, you can use `192.168.100.200.nip.io` where `192.168.100.200` is a first IP address in your network addresses range.
|
||||
- alternatively you can leave the default value, however you'll be need to modify your `/etc/hosts` every time you want to access specific application.
|
||||
- Set `etcd`, `monitoring` and `ingress` to enabled position
|
||||
- Click Deploy
|
||||
|
||||
|
||||
Check persistent volumes provisioned:
|
||||
|
||||
```bash
|
||||
kubectl get pvc -n tenant-root
|
||||
```
|
||||
|
||||
example output:
|
||||
```console
|
||||
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS VOLUMEATTRIBUTESCLASS AGE
|
||||
data-etcd-0 Bound pvc-4cbd29cc-a29f-453d-b412-451647cd04bf 10Gi RWO local <unset> 2m10s
|
||||
data-etcd-1 Bound pvc-1579f95a-a69d-4a26-bcc2-b15ccdbede0d 10Gi RWO local <unset> 115s
|
||||
data-etcd-2 Bound pvc-907009e5-88bf-4d18-91e7-b56b0dbfb97e 10Gi RWO local <unset> 91s
|
||||
grafana-db-1 Bound pvc-7b3f4e23-228a-46fd-b820-d033ef4679af 10Gi RWO local <unset> 2m41s
|
||||
grafana-db-2 Bound pvc-ac9b72a4-f40e-47e8-ad24-f50d843b55e4 10Gi RWO local <unset> 113s
|
||||
vmselect-cachedir-vmselect-longterm-0 Bound pvc-622fa398-2104-459f-8744-565eee0a13f1 2Gi RWO local <unset> 2m21s
|
||||
vmselect-cachedir-vmselect-longterm-1 Bound pvc-fc9349f5-02b2-4e25-8bef-6cbc5cc6d690 2Gi RWO local <unset> 2m21s
|
||||
vmselect-cachedir-vmselect-shortterm-0 Bound pvc-7acc7ff6-6b9b-4676-bd1f-6867ea7165e2 2Gi RWO local <unset> 2m41s
|
||||
vmselect-cachedir-vmselect-shortterm-1 Bound pvc-e514f12b-f1f6-40ff-9838-a6bda3580eb7 2Gi RWO local <unset> 2m40s
|
||||
vmstorage-db-vmstorage-longterm-0 Bound pvc-e8ac7fc3-df0d-4692-aebf-9f66f72f9fef 10Gi RWO local <unset> 2m21s
|
||||
vmstorage-db-vmstorage-longterm-1 Bound pvc-68b5ceaf-3ed1-4e5a-9568-6b95911c7c3a 10Gi RWO local <unset> 2m21s
|
||||
vmstorage-db-vmstorage-shortterm-0 Bound pvc-cee3a2a4-5680-4880-bc2a-85c14dba9380 10Gi RWO local <unset> 2m41s
|
||||
vmstorage-db-vmstorage-shortterm-1 Bound pvc-d55c235d-cada-4c4a-8299-e5fc3f161789 10Gi RWO local <unset> 2m41s
|
||||
```
|
||||
|
||||
Check all pods are running:
|
||||
|
||||
|
||||
```bash
|
||||
kubectl get pod -n tenant-root
|
||||
```
|
||||
|
||||
example output:
|
||||
```console
|
||||
NAME READY STATUS RESTARTS AGE
|
||||
etcd-0 1/1 Running 0 2m1s
|
||||
etcd-1 1/1 Running 0 106s
|
||||
etcd-2 1/1 Running 0 82s
|
||||
grafana-db-1 1/1 Running 0 119s
|
||||
grafana-db-2 1/1 Running 0 13s
|
||||
grafana-deployment-74b5656d6-5dcvn 1/1 Running 0 90s
|
||||
grafana-deployment-74b5656d6-q5589 1/1 Running 1 (105s ago) 111s
|
||||
root-ingress-controller-6ccf55bc6d-pg79l 2/2 Running 0 2m27s
|
||||
root-ingress-controller-6ccf55bc6d-xbs6x 2/2 Running 0 2m29s
|
||||
root-ingress-defaultbackend-686bcbbd6c-5zbvp 1/1 Running 0 2m29s
|
||||
vmalert-vmalert-644986d5c-7hvwk 2/2 Running 0 2m30s
|
||||
vmalertmanager-alertmanager-0 2/2 Running 0 2m32s
|
||||
vmalertmanager-alertmanager-1 2/2 Running 0 2m31s
|
||||
vminsert-longterm-75789465f-hc6cz 1/1 Running 0 2m10s
|
||||
vminsert-longterm-75789465f-m2v4t 1/1 Running 0 2m12s
|
||||
vminsert-shortterm-78456f8fd9-wlwww 1/1 Running 0 2m29s
|
||||
vminsert-shortterm-78456f8fd9-xg7cw 1/1 Running 0 2m28s
|
||||
vmselect-longterm-0 1/1 Running 0 2m12s
|
||||
vmselect-longterm-1 1/1 Running 0 2m12s
|
||||
vmselect-shortterm-0 1/1 Running 0 2m31s
|
||||
vmselect-shortterm-1 1/1 Running 0 2m30s
|
||||
vmstorage-longterm-0 1/1 Running 0 2m12s
|
||||
vmstorage-longterm-1 1/1 Running 0 2m12s
|
||||
vmstorage-shortterm-0 1/1 Running 0 2m32s
|
||||
vmstorage-shortterm-1 1/1 Running 0 2m31s
|
||||
```
|
||||
|
||||
Now you can get public IP of ingress controller:
|
||||
```
|
||||
kubectl get svc -n tenant-root root-ingress-controller
|
||||
```
|
||||
|
||||
example output:
|
||||
```console
|
||||
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
|
||||
root-ingress-controller LoadBalancer 10.96.16.141 192.168.100.200 80:31632/TCP,443:30113/TCP 3m33s
|
||||
```
|
||||
|
||||
Use `grafana.example.org` (under 192.168.100.200) to access system monitoring, where `example.org` is your domain specified for `tenant-root`
|
||||
|
||||
- login: `admin`
|
||||
- password:
|
||||
|
||||
```bash
|
||||
kubectl get secret -n tenant-root grafana-admin-password -o go-template='{{ printf "%s\n" (index .data "password" | base64decode) }}'
|
||||
```
|
||||
[Contact us](https://aenix.io/contact/)
|
||||
|
||||
@@ -12,9 +12,6 @@ talos_version=$(awk '/^version:/ {print $2}' packages/core/installer/images/talo
|
||||
|
||||
set -x
|
||||
|
||||
sed -i "s|\(ghcr.io/aenix-io/cozystack/matchbox:\)v[^ ]\+|\1${version}|g" README.md
|
||||
sed -i "s|\(ghcr.io/aenix-io/cozystack/talos:\)v[^ ]\+|\1${talos_version}|g" README.md
|
||||
|
||||
sed -i "/^TAG / s|=.*|= ${version}|" \
|
||||
packages/apps/http-cache/Makefile \
|
||||
packages/apps/kubernetes/Makefile \
|
||||
|
||||
@@ -61,8 +61,6 @@ spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
app: cozystack
|
||||
strategy:
|
||||
type: Recreate
|
||||
template:
|
||||
metadata:
|
||||
labels:
|
||||
@@ -72,14 +70,26 @@ spec:
|
||||
serviceAccountName: cozystack
|
||||
containers:
|
||||
- name: cozystack
|
||||
image: "ghcr.io/aenix-io/cozystack/installer:v0.0.2"
|
||||
image: "ghcr.io/aenix-io/cozystack/cozystack:v0.1.0"
|
||||
env:
|
||||
- name: KUBERNETES_SERVICE_HOST
|
||||
value: localhost
|
||||
- name: KUBERNETES_SERVICE_PORT
|
||||
value: "7445"
|
||||
- name: K8S_AWAIT_ELECTION_ENABLED
|
||||
value: "1"
|
||||
- name: K8S_AWAIT_ELECTION_NAME
|
||||
value: cozystack
|
||||
- name: K8S_AWAIT_ELECTION_LOCK_NAME
|
||||
value: cozystack
|
||||
- name: K8S_AWAIT_ELECTION_LOCK_NAMESPACE
|
||||
value: cozy-system
|
||||
- name: K8S_AWAIT_ELECTION_IDENTITY
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
fieldPath: metadata.name
|
||||
- name: darkhttpd
|
||||
image: "ghcr.io/aenix-io/cozystack/installer:v0.0.2"
|
||||
image: "ghcr.io/aenix-io/cozystack/cozystack:v0.1.0"
|
||||
command:
|
||||
- /usr/bin/darkhttpd
|
||||
- /cozystack/assets
|
||||
|
||||
@@ -2,7 +2,7 @@ PUSH := 1
|
||||
LOAD := 0
|
||||
REGISTRY := ghcr.io/aenix-io/cozystack
|
||||
NGINX_CACHE_TAG = v0.1.0
|
||||
TAG := v0.0.2
|
||||
TAG := v0.2.0
|
||||
|
||||
image: image-nginx
|
||||
|
||||
|
||||
@@ -1,14 +1,4 @@
|
||||
{
|
||||
"containerimage.config.digest": "sha256:f4ad0559a74749de0d11b1835823bf9c95332962b0909450251d849113f22c19",
|
||||
"containerimage.descriptor": {
|
||||
"mediaType": "application/vnd.docker.distribution.manifest.v2+json",
|
||||
"digest": "sha256:3a0e8d791e0ccf681711766387ea9278e7d39f1956509cead2f72aa0001797ef",
|
||||
"size": 1093,
|
||||
"platform": {
|
||||
"architecture": "amd64",
|
||||
"os": "linux"
|
||||
}
|
||||
},
|
||||
"containerimage.digest": "sha256:3a0e8d791e0ccf681711766387ea9278e7d39f1956509cead2f72aa0001797ef",
|
||||
"image.name": "ghcr.io/aenix-io/cozystack/nginx-cache:v0.1.0,ghcr.io/aenix-io/cozystack/nginx-cache:v0.1.0-v0.0.2"
|
||||
"containerimage.config.digest": "sha256:318fd8d0d6f6127387042f6ad150e87023d1961c7c5059dd5324188a54b0ab4e",
|
||||
"containerimage.digest": "sha256:e3cf145238e6e45f7f13b9acaea445c94ff29f76a34ba9fa50828401a5a3cc68"
|
||||
}
|
||||
@@ -1,7 +1,7 @@
|
||||
PUSH := 1
|
||||
LOAD := 0
|
||||
REGISTRY := ghcr.io/aenix-io/cozystack
|
||||
TAG := v0.0.2
|
||||
TAG := v0.2.0
|
||||
UBUNTU_CONTAINER_DISK_TAG = v1.29.1
|
||||
|
||||
image: image-ubuntu-container-disk
|
||||
|
||||
@@ -1,4 +1,4 @@
|
||||
{
|
||||
"containerimage.config.digest": "sha256:e982cfa2320d3139ed311ae44bcc5ea18db7e4e76d2746e0af04c516288ff0f1",
|
||||
"containerimage.digest": "sha256:34f6aba5b5a2afbb46bbb891ef4ddc0855c2ffe4f9e5a99e8e553286ddd2c070"
|
||||
"containerimage.config.digest": "sha256:ee8968be63c7c45621ec45f3687211e0875acb24e8d9784e8d2ebcbf46a3538c",
|
||||
"containerimage.digest": "sha256:16c3c07e74212585786dc1f1ae31d3ab90a575014806193e8e37d1d7751cb084"
|
||||
}
|
||||
@@ -3,7 +3,7 @@ NAME=installer
|
||||
PUSH := 1
|
||||
LOAD := 0
|
||||
REGISTRY := ghcr.io/aenix-io/cozystack
|
||||
TAG := v0.0.2
|
||||
TAG := v0.2.0
|
||||
TALOS_VERSION=$(shell awk '/^version:/ {print $$2}' images/talos/profiles/installer.yaml)
|
||||
|
||||
show:
|
||||
@@ -18,18 +18,18 @@ diff:
|
||||
update:
|
||||
hack/gen-profiles.sh
|
||||
|
||||
image: image-installer image-talos image-matchbox
|
||||
image: image-cozystack image-talos image-matchbox
|
||||
|
||||
image-installer:
|
||||
docker buildx build -f images/installer/Dockerfile ../../.. \
|
||||
image-cozystack:
|
||||
docker buildx build -f images/cozystack/Dockerfile ../../.. \
|
||||
--provenance false \
|
||||
--tag $(REGISTRY)/installer:$(TAG) \
|
||||
--cache-from type=registry,ref=$(REGISTRY)/installer:$(TAG) \
|
||||
--tag $(REGISTRY)/cozystack:$(TAG) \
|
||||
--cache-from type=registry,ref=$(REGISTRY)/cozystack:$(TAG) \
|
||||
--cache-to type=inline \
|
||||
--metadata-file images/installer.json \
|
||||
--metadata-file images/cozystack.json \
|
||||
--push=$(PUSH) \
|
||||
--load=$(LOAD)
|
||||
echo "$(REGISTRY)/installer:$(TAG)" > images/installer.tag
|
||||
echo "$(REGISTRY)/cozystack:$(TAG)" > images/cozystack.tag
|
||||
|
||||
image-talos:
|
||||
test -f ../../../_out/assets/installer-amd64.tar || make talos-installer
|
||||
@@ -43,14 +43,18 @@ image-matchbox:
|
||||
docker buildx build -f images/matchbox/Dockerfile ../../.. \
|
||||
--provenance false \
|
||||
--tag $(REGISTRY)/matchbox:$(TAG) \
|
||||
--cache-from type=registry,ref=$(REGISTRY)/matchbox:$(TAG) \
|
||||
--tag $(REGISTRY)/matchbox:$(TALOS_VERSION)-$(TAG) \
|
||||
--cache-from type=registry,ref=$(REGISTRY)/matchbox:$(TALOS_VERSION) \
|
||||
--cache-to type=inline \
|
||||
--metadata-file images/matchbox.json \
|
||||
--push=$(PUSH) \
|
||||
--load=$(LOAD)
|
||||
echo "$(REGISTRY)/matchbox:$(TAG)" > images/matchbox.tag
|
||||
echo "$(REGISTRY)/matchbox:$(TALOS_VERSION)" > images/matchbox.tag
|
||||
|
||||
assets: talos-iso
|
||||
|
||||
talos-initramfs talos-kernel talos-installer talos-iso:
|
||||
cat images/talos/profiles/$(subst talos-,,$@).yaml | docker run --rm -i -v $${PWD}/../../../_out/assets:/out -v /dev:/dev --privileged "ghcr.io/siderolabs/imager:$(TALOS_VERSION)" -
|
||||
mkdir -p ../../../_out/assets
|
||||
cat images/talos/profiles/$(subst talos-,,$@).yaml | \
|
||||
docker run --rm -i -v /dev:/dev --privileged "ghcr.io/siderolabs/imager:$(TALOS_VERSION)" --tar-to-stdout - | \
|
||||
tar -C ../../../_out/assets -xzf-
|
||||
|
||||
4
packages/core/installer/images/cozystack.json
Normal file
4
packages/core/installer/images/cozystack.json
Normal file
@@ -0,0 +1,4 @@
|
||||
{
|
||||
"containerimage.config.digest": "sha256:ec8a4983a663f06a1503507482667a206e83e0d8d3663dff60ced9221855d6b0",
|
||||
"containerimage.digest": "sha256:abb7b2fbc1f143c922f2a35afc4423a74b2b63c0bddfe620750613ed835aa861"
|
||||
}
|
||||
1
packages/core/installer/images/cozystack.tag
Normal file
1
packages/core/installer/images/cozystack.tag
Normal file
@@ -0,0 +1 @@
|
||||
ghcr.io/aenix-io/cozystack/cozystack:v0.1.0
|
||||
@@ -1,3 +1,15 @@
|
||||
FROM golang:alpine3.19 as k8s-await-election-builder
|
||||
|
||||
ARG K8S_AWAIT_ELECTION_GITREPO=https://github.com/LINBIT/k8s-await-election
|
||||
ARG K8S_AWAIT_ELECTION_VERSION=0.4.1
|
||||
|
||||
RUN apk add --no-cache git make
|
||||
RUN git clone ${K8S_AWAIT_ELECTION_GITREPO} /usr/local/go/k8s-await-election/ \
|
||||
&& cd /usr/local/go/k8s-await-election \
|
||||
&& git reset --hard v${K8S_AWAIT_ELECTION_VERSION} \
|
||||
&& make \
|
||||
&& mv ./out/k8s-await-election-amd64 /k8s-await-election
|
||||
|
||||
FROM alpine:3.19 AS builder
|
||||
|
||||
RUN apk add --no-cache make git
|
||||
@@ -18,7 +30,8 @@ COPY scripts /cozystack/scripts
|
||||
COPY --from=builder /src/packages/core /cozystack/packages/core
|
||||
COPY --from=builder /src/packages/system /cozystack/packages/system
|
||||
COPY --from=builder /src/_out/repos /cozystack/assets/repos
|
||||
COPY --from=k8s-await-election-builder /k8s-await-election /usr/bin/k8s-await-election
|
||||
COPY dashboards /cozystack/assets/dashboards
|
||||
|
||||
WORKDIR /cozystack
|
||||
ENTRYPOINT [ "/cozystack/scripts/installer.sh" ]
|
||||
ENTRYPOINT ["/usr/bin/k8s-await-election", "/cozystack/scripts/installer.sh" ]
|
||||
@@ -1,14 +0,0 @@
|
||||
{
|
||||
"containerimage.config.digest": "sha256:5c7f51a9cbc945c13d52157035eba6ba4b6f3b68b76280f8e64b4f6ba239db1a",
|
||||
"containerimage.descriptor": {
|
||||
"mediaType": "application/vnd.docker.distribution.manifest.v2+json",
|
||||
"digest": "sha256:7cda3480faf0539ed4a3dd252aacc7a997645d3a390ece377c36cf55f9e57e11",
|
||||
"size": 2074,
|
||||
"platform": {
|
||||
"architecture": "amd64",
|
||||
"os": "linux"
|
||||
}
|
||||
},
|
||||
"containerimage.digest": "sha256:7cda3480faf0539ed4a3dd252aacc7a997645d3a390ece377c36cf55f9e57e11",
|
||||
"image.name": "ghcr.io/aenix-io/cozystack/installer:v0.0.2"
|
||||
}
|
||||
@@ -1 +0,0 @@
|
||||
ghcr.io/aenix-io/cozystack/installer:v0.0.2
|
||||
@@ -1,14 +1,4 @@
|
||||
{
|
||||
"containerimage.config.digest": "sha256:cb8cb211017e51f6eb55604287c45cbf6ed8add5df482aaebff3d493a11b5a76",
|
||||
"containerimage.descriptor": {
|
||||
"mediaType": "application/vnd.docker.distribution.manifest.v2+json",
|
||||
"digest": "sha256:3be72cdce2f4ab4886a70fb7b66e4518a1fe4ba0771319c96fa19a0d6f409602",
|
||||
"size": 1488,
|
||||
"platform": {
|
||||
"architecture": "amd64",
|
||||
"os": "linux"
|
||||
}
|
||||
},
|
||||
"containerimage.digest": "sha256:3be72cdce2f4ab4886a70fb7b66e4518a1fe4ba0771319c96fa19a0d6f409602",
|
||||
"image.name": "ghcr.io/aenix-io/cozystack/matchbox:v0.0.2"
|
||||
"containerimage.config.digest": "sha256:b869a6324f9c0e6d1dd48eee67cbe3842ee14efd59bdde477736ad2f90568ff7",
|
||||
"containerimage.digest": "sha256:c30b237c5fa4fbbe47e1aba56e8f99569fe865620aa1953f31fc373794123cd7"
|
||||
}
|
||||
@@ -1 +1 @@
|
||||
ghcr.io/aenix-io/cozystack/matchbox:v0.0.2
|
||||
ghcr.io/aenix-io/cozystack/matchbox:v1.6.4
|
||||
|
||||
@@ -41,8 +41,6 @@ spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
app: cozystack
|
||||
strategy:
|
||||
type: Recreate
|
||||
template:
|
||||
metadata:
|
||||
labels:
|
||||
@@ -52,14 +50,26 @@ spec:
|
||||
serviceAccountName: cozystack
|
||||
containers:
|
||||
- name: cozystack
|
||||
image: "{{ .Files.Get "images/installer.tag" | trim }}@{{ index (.Files.Get "images/installer.json" | fromJson) "containerimage.digest" }}"
|
||||
image: "{{ .Files.Get "images/cozystack.tag" | trim }}@{{ index (.Files.Get "images/cozystack.json" | fromJson) "containerimage.digest" }}"
|
||||
env:
|
||||
- name: KUBERNETES_SERVICE_HOST
|
||||
value: localhost
|
||||
- name: KUBERNETES_SERVICE_PORT
|
||||
value: "7445"
|
||||
- name: K8S_AWAIT_ELECTION_ENABLED
|
||||
value: "1"
|
||||
- name: K8S_AWAIT_ELECTION_NAME
|
||||
value: cozystack
|
||||
- name: K8S_AWAIT_ELECTION_LOCK_NAME
|
||||
value: cozystack
|
||||
- name: K8S_AWAIT_ELECTION_LOCK_NAMESPACE
|
||||
value: cozy-system
|
||||
- name: K8S_AWAIT_ELECTION_IDENTITY
|
||||
valueFrom:
|
||||
fieldRef:
|
||||
fieldPath: metadata.name
|
||||
- name: darkhttpd
|
||||
image: "{{ .Files.Get "images/installer.tag" | trim }}@{{ index (.Files.Get "images/installer.json" | fromJson) "containerimage.digest" }}"
|
||||
image: "{{ .Files.Get "images/cozystack.tag" | trim }}@{{ index (.Files.Get "images/cozystack.json" | fromJson) "containerimage.digest" }}"
|
||||
command:
|
||||
- /usr/bin/darkhttpd
|
||||
- /cozystack/assets
|
||||
|
||||
@@ -646,6 +646,20 @@ spec:
|
||||
namespace: cozy-cilium
|
||||
- name: kubeovn
|
||||
namespace: cozy-kubeovn
|
||||
{{- if .Capabilities.APIVersions.Has "source.toolkit.fluxcd.io/v1beta2" }}
|
||||
{{- with (lookup "source.toolkit.fluxcd.io/v1beta2" "HelmRepository" "cozy-public" "").items }}
|
||||
values:
|
||||
kubeapps:
|
||||
redis:
|
||||
master:
|
||||
podAnnotations:
|
||||
{{- range $index, $repo := . }}
|
||||
{{- with (($repo.status).artifact).revision }}
|
||||
repository.cozystack.io/{{ $repo.metadata.name }}: {{ quote . }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
---
|
||||
apiVersion: helm.toolkit.fluxcd.io/v2beta1
|
||||
kind: HelmRelease
|
||||
|
||||
@@ -3,7 +3,7 @@ NAMESPACE=cozy-dashboard
|
||||
PUSH := 1
|
||||
LOAD := 0
|
||||
REPOSITORY := ghcr.io/aenix-io/cozystack
|
||||
TAG := v0.0.2
|
||||
TAG := v0.2.0
|
||||
|
||||
show:
|
||||
helm template --dry-run=server -n $(NAMESPACE) $(NAME) .
|
||||
|
||||
@@ -1,4 +1,4 @@
|
||||
{
|
||||
"containerimage.config.digest": "sha256:f5a26c90226016af3a23d5fdb8b23d36b0aca97b1b2a8a1de2e37cc9d5dfeb04",
|
||||
"containerimage.digest": "sha256:c71ed8953381d8fba2aebd79d538bfc0a6933910ed626afc850c4dbef4a15182"
|
||||
"containerimage.config.digest": "sha256:51a28848a801e102b3383e6d980ac2459fa29cfd9cbc381d03c561672e94139d",
|
||||
"containerimage.digest": "sha256:4b1b4ffc7c797b8fb4ab9561e6fa0a68c00d5b0d945fe47e42ecc6e43e9af0d3"
|
||||
}
|
||||
@@ -1 +1 @@
|
||||
ghcr.io/aenix-io/cozystack/dashboard:v0.0.2
|
||||
ghcr.io/aenix-io/cozystack/dashboard:v0.1.0
|
||||
|
||||
@@ -1,4 +1,4 @@
|
||||
{
|
||||
"containerimage.config.digest": "sha256:e87d3b19a59f31b70ae9e67ab9422bf2acf8fe5c6c8c585883be16db39068023",
|
||||
"containerimage.digest": "sha256:692cd506a2eadf1cf09e94eee60986a379da7a604c4810f89c8f6c5c405c2c73"
|
||||
"containerimage.config.digest": "sha256:e522ba90c58c3dab629739fe240e42037a50bfc19442d018e957ef54f05aaa77",
|
||||
"containerimage.digest": "sha256:ea80daaedd7e782bb42641fe25b2c91fc24260b81f8e576637f3d251c9c7d087"
|
||||
}
|
||||
@@ -1 +1 @@
|
||||
ghcr.io/aenix-io/cozystack/kubeapps-apis:v0.0.2
|
||||
ghcr.io/aenix-io/cozystack/kubeapps-apis:v0.1.0
|
||||
|
||||
@@ -27,6 +27,13 @@ spec:
|
||||
$patch: delete
|
||||
- name: drbd-module-loader
|
||||
$patch: delete
|
||||
containers:
|
||||
- name: linstor-satellite
|
||||
volumeMounts:
|
||||
- mountPath: /run
|
||||
name: host-run
|
||||
securityContext:
|
||||
readOnlyRootFilesystem: false
|
||||
volumes:
|
||||
- name: run-systemd-system
|
||||
$patch: delete
|
||||
@@ -46,3 +53,7 @@ spec:
|
||||
hostPath:
|
||||
path: /var/etc/lvm/archive
|
||||
type: DirectoryOrCreate
|
||||
- name: host-run
|
||||
hostPath:
|
||||
path: /run
|
||||
type: DirectoryOrCreate
|
||||
|
||||
@@ -1,17 +1,19 @@
|
||||
apiVersion: v2
|
||||
appVersion: v0.0.22
|
||||
appVersion: v0.0.27
|
||||
description: Run and operate MariaDB in a cloud native way
|
||||
home: https://github.com/mariadb-operator/mariadb-operator
|
||||
icon: https://mariadb-operator.github.io/mariadb-operator/assets/mariadb.png
|
||||
icon: https://mariadb-operator.github.io/mariadb-operator/assets/mariadb_profile.svg
|
||||
keywords:
|
||||
- mariadb
|
||||
- mysql
|
||||
- operator
|
||||
- mariadb-operator
|
||||
- database
|
||||
- maxscale
|
||||
kubeVersion: '>= 1.16.0-0'
|
||||
maintainers:
|
||||
- email: mariadb-operator@proton.me
|
||||
name: mmontes11
|
||||
name: mariadb-operator
|
||||
type: application
|
||||
version: 0.22.0
|
||||
version: 0.27.0
|
||||
|
||||
@@ -3,10 +3,10 @@
|
||||
[//]: # (README.md generated by gotmpl. DO NOT EDIT.)
|
||||
|
||||
<p align="center">
|
||||
<img src="https://mariadb-operator.github.io/mariadb-operator/assets/mariadb-operator.png" alt="mariadb" width="250"/>
|
||||
<img src="https://mariadb-operator.github.io/mariadb-operator/assets/mariadb-operator_centered_whitebg.svg" alt="mariadb" width="100%"/>
|
||||
</p>
|
||||
|
||||
  
|
||||
  
|
||||
|
||||
Run and operate MariaDB in a cloud native way
|
||||
|
||||
@@ -26,20 +26,50 @@ helm uninstall mariadb-operator
|
||||
| Key | Type | Default | Description |
|
||||
|-----|------|---------|-------------|
|
||||
| affinity | object | `{}` | Affinity to add to controller Pod |
|
||||
| certController.affinity | object | `{}` | Affinity to add to controller Pod |
|
||||
| certController.caValidity | string | `"35064h"` | CA certificate validity. It must be greater than certValidity. |
|
||||
| certController.certValidity | string | `"8766h"` | Certificate validity. |
|
||||
| certController.enabled | bool | `true` | Specifies whether the cert-controller should be created. |
|
||||
| certController.extrArgs | list | `[]` | Extra arguments to be passed to the cert-controller entrypoint |
|
||||
| certController.extraVolumeMounts | list | `[]` | Extra volumes to mount to cert-controller container |
|
||||
| certController.extraVolumes | list | `[]` | Extra volumes to pass to cert-controller Pod |
|
||||
| certController.ha.enabled | bool | `false` | Enable high availability |
|
||||
| certController.ha.replicas | int | `3` | Number of replicas |
|
||||
| certController.image.pullPolicy | string | `"IfNotPresent"` | |
|
||||
| certController.image.repository | string | `"ghcr.io/mariadb-operator/mariadb-operator"` | |
|
||||
| certController.image.tag | string | `""` | Image tag to use. By default the chart appVersion is used |
|
||||
| certController.imagePullSecrets | list | `[]` | |
|
||||
| certController.lookaheadValidity | string | `"2160h"` | Duration used to verify whether a certificate is valid or not. |
|
||||
| certController.nodeSelector | object | `{}` | Node selectors to add to controller Pod |
|
||||
| certController.podAnnotations | object | `{}` | Annotations to add to cert-controller Pod |
|
||||
| certController.podSecurityContext | object | `{}` | Security context to add to cert-controller Pod |
|
||||
| certController.requeueDuration | string | `"5m"` | Requeue duration to ensure that certificate gets renewed. |
|
||||
| certController.resources | object | `{}` | Resources to add to cert-controller container |
|
||||
| certController.securityContext | object | `{}` | Security context to add to cert-controller container |
|
||||
| certController.serviceAccount.annotations | object | `{}` | Annotations to add to the service account |
|
||||
| certController.serviceAccount.automount | bool | `true` | Automounts the service account token in all containers of the Pod |
|
||||
| certController.serviceAccount.enabled | bool | `true` | Specifies whether a service account should be created |
|
||||
| certController.serviceAccount.extraLabels | object | `{}` | Extra Labels to add to the service account |
|
||||
| certController.serviceAccount.name | string | `""` | The name of the service account to use. If not set and enabled is true, a name is generated using the fullname template |
|
||||
| certController.serviceMonitor.additionalLabels | object | `{}` | Labels to be added to the cert-controller ServiceMonitor |
|
||||
| certController.serviceMonitor.enabled | bool | `true` | Enable cert-controller ServiceMonitor. Metrics must be enabled |
|
||||
| certController.serviceMonitor.interval | string | `"30s"` | Interval to scrape metrics |
|
||||
| certController.serviceMonitor.scrapeTimeout | string | `"25s"` | Timeout if metrics can't be retrieved in given time interval |
|
||||
| certController.tolerations | list | `[]` | Tolerations to add to controller Pod |
|
||||
| clusterName | string | `"cluster.local"` | Cluster DNS name |
|
||||
| extrArgs | list | `[]` | Extra arguments to be passed to the controller entrypoint |
|
||||
| extraEnv | list | `[]` | Extra environment variables to be passed to the controller |
|
||||
| extraVolumeMounts | list | `[]` | Extra volumes to mount to the container. |
|
||||
| extraVolumes | list | `[]` | Extra volumes to pass to pod. |
|
||||
| fullnameOverride | string | `""` | |
|
||||
| ha.enabled | bool | `false` | Enable high availability |
|
||||
| ha.leaseId | string | `"mariadb.mmontes.io"` | Lease resource name to be used for leader election |
|
||||
| ha.replicas | int | `3` | Number of replicas |
|
||||
| image.pullPolicy | string | `"IfNotPresent"` | |
|
||||
| image.repository | string | `"ghcr.io/mariadb-operator/mariadb-operator"` | |
|
||||
| image.tag | string | `""` | Image tag to use. By default the chart appVersion is used |
|
||||
| imagePullSecrets | list | `[]` | |
|
||||
| logLevel | string | `"INFO"` | Controller log level |
|
||||
| metrics.enabled | bool | `false` | Enable prometheus metrics. Prometheus must be installed in the cluster |
|
||||
| metrics.enabled | bool | `false` | Enable operator internal metrics. Prometheus must be installed in the cluster |
|
||||
| metrics.serviceMonitor.additionalLabels | object | `{}` | Labels to be added to the controller ServiceMonitor |
|
||||
| metrics.serviceMonitor.enabled | bool | `true` | Enable controller ServiceMonitor |
|
||||
| metrics.serviceMonitor.interval | string | `"30s"` | Interval to scrape metrics |
|
||||
@@ -59,16 +89,19 @@ helm uninstall mariadb-operator
|
||||
| tolerations | list | `[]` | Tolerations to add to controller Pod |
|
||||
| webhook.affinity | object | `{}` | Affinity to add to controller Pod |
|
||||
| webhook.annotations | object | `{}` | Annotations for webhook configurations. |
|
||||
| webhook.certificate.certManager | bool | `false` | Use cert-manager to issue and rotate the certificate. If set to false, a default certificate will be used. |
|
||||
| webhook.certificate.default | object | `{"annotations":{},"caExpirationDays":365,"certExpirationDays":365,"hook":""}` | Default certificate generated when the chart is installed or upgraded. |
|
||||
| webhook.certificate.default.annotations | object | `{}` | Annotations for certificate Secret. |
|
||||
| webhook.certificate.default.caExpirationDays | int | `365` | Certificate authority expiration in days. |
|
||||
| webhook.certificate.default.certExpirationDays | int | `365` | Certificate expiration in days. |
|
||||
| webhook.certificate.default.hook | string | `""` | Helm hook to be added to the default certificate. |
|
||||
| webhook.certificate.path | string | `"/tmp/k8s-webhook-server/serving-certs"` | Path where the certificate will be mounted. |
|
||||
| webhook.cert.caPath | string | `"/tmp/k8s-webhook-server/certificate-authority"` | Path where the CA certificate will be mounted. |
|
||||
| webhook.cert.certManager.duration | string | `""` | Duration to be used in the Certificate resource, |
|
||||
| webhook.cert.certManager.enabled | bool | `false` | Whether to use cert-manager to issue and rotate the certificate. If set to false, mariadb-operator's cert-controller will be used instead. |
|
||||
| webhook.cert.certManager.issuerRef | object | `{}` | Issuer reference to be used in the Certificate resource. If not provided, a self-signed issuer will be used. |
|
||||
| webhook.cert.certManager.renewBefore | string | `""` | Renew before duration to be used in the Certificate resource. |
|
||||
| webhook.cert.path | string | `"/tmp/k8s-webhook-server/serving-certs"` | Path where the certificate will be mounted. |
|
||||
| webhook.cert.secretAnnotations | object | `{}` | Annotatioms to be added to webhook TLS secret. |
|
||||
| webhook.cert.secretLabels | object | `{}` | Labels to be added to webhook TLS secret. |
|
||||
| webhook.extrArgs | list | `[]` | Extra arguments to be passed to the webhook entrypoint |
|
||||
| webhook.extraVolumeMounts | list | `[]` | Extra volumes to mount to webhook container |
|
||||
| webhook.extraVolumes | list | `[]` | Extra volumes to pass to webhook Pod |
|
||||
| webhook.ha.enabled | bool | `false` | Enable high availability |
|
||||
| webhook.ha.replicas | int | `3` | Number of replicas |
|
||||
| webhook.hostNetwork | bool | `false` | Expose the webhook server in the host network |
|
||||
| webhook.image.pullPolicy | string | `"IfNotPresent"` | |
|
||||
| webhook.image.repository | string | `"ghcr.io/mariadb-operator/mariadb-operator"` | |
|
||||
@@ -77,7 +110,7 @@ helm uninstall mariadb-operator
|
||||
| webhook.nodeSelector | object | `{}` | Node selectors to add to controller Pod |
|
||||
| webhook.podAnnotations | object | `{}` | Annotations to add to webhook Pod |
|
||||
| webhook.podSecurityContext | object | `{}` | Security context to add to webhook Pod |
|
||||
| webhook.port | int | `10250` | Port to be used by the webhook server |
|
||||
| webhook.port | int | `9443` | Port to be used by the webhook server |
|
||||
| webhook.resources | object | `{}` | Resources to add to webhook container |
|
||||
| webhook.securityContext | object | `{}` | Security context to add to webhook container |
|
||||
| webhook.serviceAccount.annotations | object | `{}` | Annotations to add to the service account |
|
||||
|
||||
@@ -4,7 +4,7 @@
|
||||
[//]: # (README.md generated by gotmpl. DO NOT EDIT.)
|
||||
|
||||
<p align="center">
|
||||
<img src="https://mariadb-operator.github.io/mariadb-operator/assets/mariadb-operator.png" alt="mariadb" width="250"/>
|
||||
<img src="https://mariadb-operator.github.io/mariadb-operator/assets/mariadb-operator_centered_whitebg.svg" alt="mariadb" width="100%"/>
|
||||
</p>
|
||||
|
||||
{{ template "chart.typeBadge" . }}{{ template "chart.versionBadge" . }}{{ template "chart.appVersionBadge" . }}
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@@ -71,28 +71,23 @@ app.kubernetes.io/instance: {{ .Release.Name }}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Webhook certificate
|
||||
Cert-controller common labels
|
||||
*/}}
|
||||
{{- define "mariadb-operator-webhook.certificate" -}}
|
||||
{{- if .Values.webhook.certificate.certManager }}
|
||||
{{- include "mariadb-operator.fullname" . }}-webhook-cert
|
||||
{{- else }}
|
||||
{{- include "mariadb-operator.fullname" . }}-webhook-default-cert
|
||||
{{- end }}
|
||||
{{- define "mariadb-operator-cert-controller.labels" -}}
|
||||
helm.sh/chart: {{ include "mariadb-operator.chart" . }}
|
||||
{{ include "mariadb-operator-cert-controller.selectorLabels" . }}
|
||||
{{ if .Chart.AppVersion }}
|
||||
app.kubernetes.io/version: {{ .Chart.AppVersion | quote }}
|
||||
{{ end }}
|
||||
app.kubernetes.io/managed-by: {{ .Release.Service }}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Webhook certificate subject name
|
||||
Cert-controller selector labels
|
||||
*/}}
|
||||
{{- define "mariadb-operator-webhook.subjectName" -}}
|
||||
{{- include "mariadb-operator.fullname" . }}-webhook.{{ .Release.Namespace }}.svc
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Webhook certificate subject alternative name
|
||||
*/}}
|
||||
{{- define "mariadb-operator-webhook.altName" -}}
|
||||
{{- include "mariadb-operator.fullname" . }}-webhook.{{ .Release.Namespace }}.svc.{{ .Values.clusterName }}
|
||||
{{- define "mariadb-operator-cert-controller.selectorLabels" -}}
|
||||
app.kubernetes.io/name: {{ include "mariadb-operator.name" . }}-cert-controller
|
||||
app.kubernetes.io/instance: {{ .Release.Name }}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
@@ -116,3 +111,14 @@ Create the name of the webhook service account to use
|
||||
{{- default "default" .Values.webhook.serviceAccount.name }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create the name of the cert-controller service account to use
|
||||
*/}}
|
||||
{{- define "mariadb-operator-cert-controller.serviceAccountName" -}}
|
||||
{{- if .Values.certController.serviceAccount.enabled }}
|
||||
{{- default (printf "%s-cert-controller" (include "mariadb-operator.fullname" .)) .Values.certController.serviceAccount.name }}
|
||||
{{- else }}
|
||||
{{- default "default" .Values.certController.serviceAccount.name }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@@ -0,0 +1,103 @@
|
||||
{{- if and .Values.certController.enabled (not .Values.webhook.cert.certManager.enabled) -}}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
name: {{ include "mariadb-operator.fullname" . }}-cert-controller
|
||||
labels:
|
||||
{{ include "mariadb-operator-cert-controller.labels" . | nindent 4 }}
|
||||
spec:
|
||||
{{ if .Values.certController.ha.enabled }}
|
||||
replicas: {{ .Values.certController.ha.replicas}}
|
||||
{{ end }}
|
||||
selector:
|
||||
matchLabels:
|
||||
{{ include "mariadb-operator-cert-controller.selectorLabels" . | nindent 6 }}
|
||||
template:
|
||||
metadata:
|
||||
{{ with .Values.certController.podAnnotations }}
|
||||
annotations:
|
||||
{{ toYaml . | nindent 8 }}
|
||||
{{ end }}
|
||||
labels:
|
||||
{{ include "mariadb-operator-cert-controller.selectorLabels" . | nindent 8 }}
|
||||
spec:
|
||||
{{- with .Values.certController.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
serviceAccountName: {{ include "mariadb-operator-cert-controller.serviceAccountName" . }}-cert-controller
|
||||
automountServiceAccountToken: {{ .Values.certController.serviceAccount.automount }}
|
||||
{{ with .Values.certController.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{ toYaml . | nindent 8 }}
|
||||
{{ end }}
|
||||
{{ with .Values.certController.tolerations }}
|
||||
tolerations:
|
||||
{{ toYaml . | nindent 8 }}
|
||||
{{ end }}
|
||||
{{ with .Values.certController.affinity }}
|
||||
affinity:
|
||||
{{ toYaml . | nindent 8 }}
|
||||
{{ end }}
|
||||
{{ with .Values.certController.podSecurityContext }}
|
||||
securityContext:
|
||||
{{ toYaml . | nindent 8 }}
|
||||
{{ end }}
|
||||
containers:
|
||||
- image: "{{ .Values.certController.image.repository }}:{{ .Values.certController.image.tag | default .Chart.AppVersion }}"
|
||||
imagePullPolicy: {{ .Values.certController.image.pullPolicy }}
|
||||
name: cert-controller
|
||||
args:
|
||||
- cert-controller
|
||||
- --ca-secret-name={{ include "mariadb-operator.fullname" . }}-webhook-ca
|
||||
- --ca-secret-namespace={{ .Release.Namespace }}
|
||||
- --ca-validity={{ .Values.certController.caValidity }}
|
||||
- --cert-secret-name={{ include "mariadb-operator.fullname" . }}-webhook-cert
|
||||
- --cert-secret-namespace={{ .Release.Namespace }}
|
||||
- --cert-validity={{ .Values.certController.certValidity }}
|
||||
- --lookahead-validity={{ .Values.certController.lookaheadValidity }}
|
||||
- --service-name={{ include "mariadb-operator.fullname" . }}-webhook
|
||||
- --service-namespace={{ .Release.Namespace }}
|
||||
- --requeue-duration={{ .Values.certController.requeueDuration }}
|
||||
- --metrics-addr=:8080
|
||||
- --health-addr=:8081
|
||||
- --log-level={{ .Values.logLevel }}
|
||||
{{- if .Values.certController.ha.enabled }}
|
||||
- --leader-elect
|
||||
{{- end }}
|
||||
{{- range .Values.certController.extrArgs }}
|
||||
- {{ . }}
|
||||
{{- end }}
|
||||
ports:
|
||||
- containerPort: 8080
|
||||
protocol: TCP
|
||||
name: metrics
|
||||
- containerPort: 8081
|
||||
protocol: TCP
|
||||
name: health
|
||||
env:
|
||||
- name: CLUSTER_NAME
|
||||
value: {{ .Values.clusterName }}
|
||||
{{- with .Values.certController.extraVolumeMounts }}
|
||||
volumeMounts:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
readinessProbe:
|
||||
httpGet:
|
||||
path: /readyz
|
||||
port: 8081
|
||||
initialDelaySeconds: 20
|
||||
periodSeconds: 5
|
||||
{{ with .Values.certController.resources }}
|
||||
resources:
|
||||
{{ toYaml . | nindent 12 }}
|
||||
{{ end }}
|
||||
{{ with .Values.certController.securityContext}}
|
||||
securityContext:
|
||||
{{ toYaml . | nindent 12 }}
|
||||
{{ end }}
|
||||
{{- with .Values.certController.extraVolumes }}
|
||||
volumes:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@@ -0,0 +1,88 @@
|
||||
{{- if and .Values.rbac.enabled .Values.certController.enabled (not .Values.webhook.cert.certManager.enabled) -}}
|
||||
{{ $fullName := include "mariadb-operator.fullname" . }}
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: Role
|
||||
metadata:
|
||||
name: {{ $fullName }}-cert-controller
|
||||
rules:
|
||||
- apiGroups:
|
||||
- coordination.k8s.io
|
||||
resources:
|
||||
- leases
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- create
|
||||
- update
|
||||
- patch
|
||||
- delete
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- events
|
||||
verbs:
|
||||
- create
|
||||
- patch
|
||||
---
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRole
|
||||
metadata:
|
||||
name: {{ $fullName }}-cert-controller
|
||||
rules:
|
||||
- apiGroups:
|
||||
- admissionregistration.k8s.io
|
||||
resources:
|
||||
- validatingwebhookconfigurations
|
||||
- mutatingwebhookconfigurations
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- secrets
|
||||
verbs:
|
||||
- create
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- endpoints
|
||||
- endpoints/restricted
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
---
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: RoleBinding
|
||||
metadata:
|
||||
name: {{ $fullName }}-cert-controller
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: Role
|
||||
name: {{ $fullName }}-cert-controller
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: {{ include "mariadb-operator-cert-controller.serviceAccountName" . }}-cert-controller
|
||||
namespace: {{ .Release.Namespace }}
|
||||
---
|
||||
apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: ClusterRoleBinding
|
||||
metadata:
|
||||
name: {{ $fullName }}-cert-controller
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: ClusterRole
|
||||
name: {{ $fullName }}-cert-controller
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: {{ include "mariadb-operator-cert-controller.serviceAccountName" . }}-cert-controller
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
@@ -0,0 +1,15 @@
|
||||
{{- if and .Values.certController.enabled (not .Values.webhook.cert.certManager.enabled) -}}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: {{ include "mariadb-operator-cert-controller.serviceAccountName" . }}-cert-controller
|
||||
labels:
|
||||
{{- include "mariadb-operator-cert-controller.labels" . | nindent 4 }}
|
||||
{{- with .Values.certController.serviceAccount.extraLabels }}
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- with .Values.certController.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@@ -0,0 +1,36 @@
|
||||
{{ if and .Values.certController.enabled (not .Values.webhook.cert.certManager.enabled) .Values.metrics.enabled .Values.certController.serviceMonitor.enabled }}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
metadata:
|
||||
name: {{ include "mariadb-operator.fullname" . }}-cert-controller-metrics
|
||||
labels:
|
||||
{{ include "mariadb-operator-cert-controller.labels" . | nindent 4 }}
|
||||
spec:
|
||||
ports:
|
||||
- port: 8080
|
||||
protocol: TCP
|
||||
name: metrics
|
||||
selector:
|
||||
{{ include "mariadb-operator-cert-controller.selectorLabels" . | nindent 4 }}
|
||||
---
|
||||
apiVersion: monitoring.coreos.com/v1
|
||||
kind: ServiceMonitor
|
||||
metadata:
|
||||
name: {{ include "mariadb-operator.fullname" . }}-cert-controller
|
||||
labels:
|
||||
{{ include "mariadb-operator-cert-controller.labels" . | nindent 4 }}
|
||||
{{ with .Values.certController.serviceMonitor.additionalLabels }}
|
||||
{{ toYaml . | nindent 4 }}
|
||||
{{ end }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
{{ include "mariadb-operator-cert-controller.selectorLabels" . | nindent 6 }}
|
||||
namespaceSelector:
|
||||
matchNames:
|
||||
- {{ .Release.Namespace | quote }}
|
||||
endpoints:
|
||||
- port: metrics
|
||||
interval: {{ .Values.certController.serviceMonitor.interval }}
|
||||
scrapeTimeout: {{ .Values.certController.serviceMonitor.scrapeTimeout }}
|
||||
{{ end }}
|
||||
@@ -0,0 +1,13 @@
|
||||
apiVersion: v1
|
||||
data:
|
||||
MARIADB_GALERA_AGENT_IMAGE: ghcr.io/mariadb-operator/mariadb-operator:v0.0.27
|
||||
MARIADB_GALERA_INIT_IMAGE: ghcr.io/mariadb-operator/mariadb-operator:v0.0.27
|
||||
MARIADB_GALERA_LIB_PATH: /usr/lib/galera/libgalera_smm.so
|
||||
MARIADB_OPERATOR_IMAGE: ghcr.io/mariadb-operator/mariadb-operator:v0.0.27
|
||||
RELATED_IMAGE_EXPORTER: prom/mysqld-exporter:v0.15.1
|
||||
RELATED_IMAGE_MARIADB: mariadb:11.2.2
|
||||
RELATED_IMAGE_MAXSCALE: mariadb/maxscale:23.08
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
creationTimestamp: null
|
||||
name: mariadb-operator-env
|
||||
@@ -53,17 +53,17 @@ spec:
|
||||
{{- if .Values.ha.enabled }}
|
||||
- --leader-elect
|
||||
{{- end }}
|
||||
{{- if .Values.metrics.enabled }}
|
||||
- --service-monitor-reconciler
|
||||
{{- end }}
|
||||
{{- range .Values.extrArgs }}
|
||||
{{- range .Values.extraArgs }}
|
||||
- {{ . }}
|
||||
{{- end }}
|
||||
ports:
|
||||
- containerPort: 8080
|
||||
protocol: TCP
|
||||
name: metrics
|
||||
env:
|
||||
envFrom:
|
||||
- configMapRef:
|
||||
name: mariadb-operator-env
|
||||
env:
|
||||
- name: CLUSTER_NAME
|
||||
value: {{ .Values.clusterName }}
|
||||
- name: MARIADB_OPERATOR_NAME
|
||||
@@ -76,6 +76,9 @@ spec:
|
||||
fieldPath: metadata.namespace
|
||||
- name: MARIADB_OPERATOR_SA_PATH
|
||||
value: /var/run/secrets/kubernetes.io/serviceaccount/token
|
||||
{{- with .Values.extraEnv }}
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
{{- if .Values.extraVolumeMounts }}
|
||||
volumeMounts:
|
||||
{{- toYaml .Values.extraVolumeMounts | nindent 12 }}
|
||||
@@ -88,21 +91,6 @@ spec:
|
||||
securityContext:
|
||||
{{ toYaml . | nindent 12 }}
|
||||
{{ end }}
|
||||
readinessProbe:
|
||||
tcpSocket:
|
||||
port: 8080
|
||||
initialDelaySeconds: 30
|
||||
periodSeconds: 10
|
||||
livenessProbe:
|
||||
tcpSocket:
|
||||
port: 8080
|
||||
initialDelaySeconds: 30
|
||||
periodSeconds: 10
|
||||
startupProbe:
|
||||
tcpSocket:
|
||||
port: 8080
|
||||
initialDelaySeconds: 20
|
||||
periodSeconds: 10
|
||||
{{- if .Values.extraVolumes }}
|
||||
volumes:
|
||||
{{- toYaml .Values.extraVolumes | nindent 8 }}
|
||||
|
||||
@@ -56,6 +56,15 @@ rules:
|
||||
- ""
|
||||
resources:
|
||||
- endpoints
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- endpoints/restricted
|
||||
verbs:
|
||||
- create
|
||||
@@ -90,6 +99,12 @@ rules:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- pvcs
|
||||
verbs:
|
||||
- list
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
@@ -117,16 +132,38 @@ rules:
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- apps
|
||||
resources:
|
||||
- deployments
|
||||
verbs:
|
||||
- create
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- apps
|
||||
resources:
|
||||
- statefulsets
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- authentication.k8s.io
|
||||
resources:
|
||||
- tokenreviews
|
||||
verbs:
|
||||
- create
|
||||
- apiGroups:
|
||||
- authorization.k8s.io
|
||||
resources:
|
||||
- subjectaccessreviews
|
||||
verbs:
|
||||
- create
|
||||
- apiGroups:
|
||||
- batch
|
||||
resources:
|
||||
@@ -142,11 +179,12 @@ rules:
|
||||
- jobs
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- backups
|
||||
verbs:
|
||||
@@ -158,13 +196,13 @@ rules:
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- backups/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- backups/status
|
||||
verbs:
|
||||
@@ -172,7 +210,7 @@ rules:
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- connections
|
||||
verbs:
|
||||
@@ -184,23 +222,37 @@ rules:
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- connections
|
||||
- grants
|
||||
- maxscale
|
||||
- restores
|
||||
- users
|
||||
verbs:
|
||||
- create
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- connections
|
||||
- grants
|
||||
- users
|
||||
verbs:
|
||||
- create
|
||||
- list
|
||||
- patch
|
||||
- watch
|
||||
- apiGroups:
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- connections/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- connections/status
|
||||
verbs:
|
||||
@@ -208,7 +260,7 @@ rules:
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- databases
|
||||
verbs:
|
||||
@@ -220,13 +272,13 @@ rules:
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- databases/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- databases/status
|
||||
verbs:
|
||||
@@ -234,7 +286,7 @@ rules:
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- grants
|
||||
verbs:
|
||||
@@ -246,13 +298,13 @@ rules:
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- grants/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- grants/status
|
||||
verbs:
|
||||
@@ -260,7 +312,7 @@ rules:
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- mariadbs
|
||||
verbs:
|
||||
@@ -272,13 +324,13 @@ rules:
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- mariadbs/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- mariadbs/status
|
||||
verbs:
|
||||
@@ -286,7 +338,33 @@ rules:
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- maxscales
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- maxscales/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- maxscales/status
|
||||
verbs:
|
||||
- get
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- restores
|
||||
verbs:
|
||||
@@ -298,13 +376,13 @@ rules:
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- restores/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- restores/status
|
||||
verbs:
|
||||
@@ -312,7 +390,7 @@ rules:
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- sqljobs
|
||||
verbs:
|
||||
@@ -324,13 +402,13 @@ rules:
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- sqljobs/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- sqljobs/status
|
||||
verbs:
|
||||
@@ -338,7 +416,7 @@ rules:
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- users
|
||||
verbs:
|
||||
@@ -350,13 +428,13 @@ rules:
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- users/finalizers
|
||||
verbs:
|
||||
- update
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
resources:
|
||||
- users/status
|
||||
verbs:
|
||||
@@ -431,4 +509,4 @@ subjects:
|
||||
- kind: ServiceAccount
|
||||
name: {{ include "mariadb-operator.serviceAccountName" . }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
||||
@@ -1,4 +1,5 @@
|
||||
{{ if .Values.webhook.certificate.certManager }}
|
||||
{{ if .Values.webhook.cert.certManager.enabled }}
|
||||
{{ if not .Values.webhook.cert.certManager.issuerRef }}
|
||||
apiVersion: cert-manager.io/v1
|
||||
kind: Issuer
|
||||
metadata:
|
||||
@@ -7,6 +8,7 @@ metadata:
|
||||
{{ include "mariadb-operator-webhook.labels" . | nindent 4 }}
|
||||
spec:
|
||||
selfSigned: {}
|
||||
{{ end }}
|
||||
---
|
||||
apiVersion: cert-manager.io/v1
|
||||
kind: Certificate
|
||||
@@ -15,11 +17,33 @@ metadata:
|
||||
labels:
|
||||
{{ include "mariadb-operator-webhook.labels" . | nindent 4 }}
|
||||
spec:
|
||||
commonName: {{ include "mariadb-operator.fullname" . }}-webhook.{{ .Release.Namespace }}.svc
|
||||
dnsNames:
|
||||
- {{ include "mariadb-operator-webhook.subjectName" . }}
|
||||
- {{ include "mariadb-operator-webhook.altName" . }}
|
||||
- {{ include "mariadb-operator.fullname" . }}-webhook.{{ .Release.Namespace }}.svc.{{ .Values.clusterName }}
|
||||
- {{ include "mariadb-operator.fullname" . }}-webhook.{{ .Release.Namespace }}.svc
|
||||
- {{ include "mariadb-operator.fullname" . }}-webhook.{{ .Release.Namespace }}
|
||||
- {{ include "mariadb-operator.fullname" . }}-webhook
|
||||
issuerRef:
|
||||
{{- if .Values.webhook.cert.certManager.issuerRef -}}
|
||||
{{ toYaml .Values.webhook.cert.certManager.issuerRef | nindent 4 }}
|
||||
{{- else }}
|
||||
kind: Issuer
|
||||
name: {{ include "mariadb-operator.fullname" . }}-selfsigned-issuer
|
||||
{{- end }}
|
||||
{{- with .Values.webhook.cert.certManager.duration }}
|
||||
duration: {{ . | quote }}
|
||||
{{- end }}
|
||||
{{- with .Values.webhook.cert.certManager.renewBefore }}
|
||||
renewBefore: {{ . | quote }}
|
||||
{{- end }}
|
||||
secretName: {{ include "mariadb-operator.fullname" . }}-webhook-cert
|
||||
{{ end }}
|
||||
secretTemplate:
|
||||
{{- with .Values.webhook.cert.secretLabels }}
|
||||
labels:
|
||||
{{- toYaml . | nindent 6 }}
|
||||
{{- end }}
|
||||
{{- with .Values.webhook.cert.secretAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{ end }}
|
||||
|
||||
@@ -1,30 +1,4 @@
|
||||
{{ $fullName := include "mariadb-operator.fullname" . }}
|
||||
{{ $subjectName := include "mariadb-operator-webhook.subjectName" . }}
|
||||
{{ $altNames := list }}
|
||||
{{ $altNames := append $altNames $subjectName }}
|
||||
{{ $altNames := append $altNames (include "mariadb-operator-webhook.altName" . ) }}
|
||||
{{ $ca := genCA $fullName (.Values.webhook.certificate.default.caExpirationDays | int) }}
|
||||
{{ $cert := genSignedCert $subjectName nil $altNames (.Values.webhook.certificate.default.certExpirationDays | int) $ca }}
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
type: kubernetes.io/tls
|
||||
metadata:
|
||||
name: {{ $fullName }}-webhook-default-cert
|
||||
labels:
|
||||
{{ include "mariadb-operator-webhook.labels" . | nindent 4 }}
|
||||
annotations:
|
||||
{{ with .Values.webhook.certificate.default.hook }}
|
||||
helm.sh/hook: {{ . }}
|
||||
{{ end }}
|
||||
{{ with .Values.webhook.certificate.default.annotations }}
|
||||
{{ toYaml . | nindent 4 }}
|
||||
{{ end }}
|
||||
data:
|
||||
tls.crt: {{ $cert.Cert | b64enc }}
|
||||
tls.key: {{ $cert.Key | b64enc }}
|
||||
{{ end }}
|
||||
---
|
||||
apiVersion: admissionregistration.k8s.io/v1
|
||||
kind: MutatingWebhookConfiguration
|
||||
metadata:
|
||||
@@ -32,12 +6,11 @@ metadata:
|
||||
labels:
|
||||
{{ include "mariadb-operator-webhook.labels" . | nindent 4 }}
|
||||
annotations:
|
||||
{{ if .Values.webhook.certificate.certManager }}
|
||||
{{- if .Values.webhook.cert.certManager.enabled }}
|
||||
cert-manager.io/inject-ca-from: {{ .Release.Namespace }}/{{ include "mariadb-operator.fullname" . }}-webhook-cert
|
||||
{{ end }}
|
||||
{{ with .Values.webhook.certificate.default.hook }}
|
||||
helm.sh/hook: {{ . }}
|
||||
{{ end }}
|
||||
{{- else }}
|
||||
k8s.mariadb.com/webhook: ""
|
||||
{{- end }}
|
||||
{{ with .Values.webhook.annotations }}
|
||||
{{ toYaml . | indent 4 }}
|
||||
{{ end }}
|
||||
@@ -48,15 +21,12 @@ webhooks:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /mutate-mariadb-mmontes-io-v1alpha1-mariadb
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /mutate-k8s-mariadb-com-v1alpha1-mariadb
|
||||
failurePolicy: Fail
|
||||
name: mmariadb.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
@@ -73,12 +43,11 @@ metadata:
|
||||
labels:
|
||||
{{ include "mariadb-operator-webhook.labels" . | nindent 4 }}
|
||||
annotations:
|
||||
{{ if .Values.webhook.certificate.certManager }}
|
||||
{{- if .Values.webhook.cert.certManager.enabled }}
|
||||
cert-manager.io/inject-ca-from: {{ .Release.Namespace }}/{{ include "mariadb-operator.fullname" . }}-webhook-cert
|
||||
{{ end }}
|
||||
{{ with .Values.webhook.certificate.default.hook }}
|
||||
helm.sh/hook: {{ . }}
|
||||
{{ end }}
|
||||
{{- else }}
|
||||
k8s.mariadb.com/webhook: ""
|
||||
{{- end }}
|
||||
{{ with .Values.webhook.annotations }}
|
||||
{{ toYaml . | indent 4 }}
|
||||
{{ end }}
|
||||
@@ -89,15 +58,12 @@ webhooks:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-mariadb-mmontes-io-v1alpha1-backup
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-backup
|
||||
failurePolicy: Fail
|
||||
name: vbackup.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
@@ -112,15 +78,12 @@ webhooks:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-mariadb-mmontes-io-v1alpha1-connection
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-connection
|
||||
failurePolicy: Fail
|
||||
name: vconnection.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
@@ -135,15 +98,12 @@ webhooks:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-mariadb-mmontes-io-v1alpha1-database
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-database
|
||||
failurePolicy: Fail
|
||||
name: vdatabase.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
@@ -158,15 +118,12 @@ webhooks:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-mariadb-mmontes-io-v1alpha1-grant
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-grant
|
||||
failurePolicy: Fail
|
||||
name: vgrant.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
@@ -181,15 +138,12 @@ webhooks:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-mariadb-mmontes-io-v1alpha1-mariadb
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-mariadb
|
||||
failurePolicy: Fail
|
||||
name: vmariadb.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
@@ -198,21 +152,38 @@ webhooks:
|
||||
resources:
|
||||
- mariadbs
|
||||
sideEffects: None
|
||||
- admissionReviewVersions:
|
||||
- v1
|
||||
clientConfig:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-maxscale
|
||||
failurePolicy: Fail
|
||||
name: vmaxscale.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
- CREATE
|
||||
- UPDATE
|
||||
resources:
|
||||
- maxscales
|
||||
sideEffects: None
|
||||
- admissionReviewVersions:
|
||||
- v1
|
||||
clientConfig:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-mariadb-mmontes-io-v1alpha1-restore
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-restore
|
||||
failurePolicy: Fail
|
||||
name: vrestore.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
@@ -227,15 +198,12 @@ webhooks:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-mariadb-mmontes-io-v1alpha1-sqljob
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-sqljob
|
||||
failurePolicy: Fail
|
||||
name: vsqljob.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
@@ -250,15 +218,12 @@ webhooks:
|
||||
service:
|
||||
name: {{ $fullName }}-webhook
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-mariadb-mmontes-io-v1alpha1-user
|
||||
{{ if not .Values.webhook.certificate.certManager }}
|
||||
caBundle: {{ $ca.Cert | b64enc }}
|
||||
{{ end }}
|
||||
path: /validate-k8s-mariadb-com-v1alpha1-user
|
||||
failurePolicy: Fail
|
||||
name: vuser.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- mariadb.mmontes.io
|
||||
- k8s.mariadb.com
|
||||
apiVersions:
|
||||
- v1alpha1
|
||||
operations:
|
||||
|
||||
@@ -1,10 +1,14 @@
|
||||
{{ $fullName := include "mariadb-operator.fullname" . }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
name: {{ include "mariadb-operator.fullname" . }}-webhook
|
||||
name: {{ $fullName }}-webhook
|
||||
labels:
|
||||
{{ include "mariadb-operator-webhook.labels" . | nindent 4 }}
|
||||
spec:
|
||||
{{ if .Values.webhook.ha.enabled }}
|
||||
replicas: {{ .Values.webhook.ha.replicas}}
|
||||
{{ end }}
|
||||
selector:
|
||||
matchLabels:
|
||||
{{ include "mariadb-operator-webhook.selectorLabels" . | nindent 6 }}
|
||||
@@ -46,12 +50,18 @@ spec:
|
||||
name: webhook
|
||||
args:
|
||||
- webhook
|
||||
- --cert-dir={{ .Values.webhook.certificate.path }}
|
||||
{{- if .Values.webhook.cert.certManager.enabled }}
|
||||
- --ca-cert-path={{ .Values.webhook.cert.path }}/ca.crt
|
||||
{{- else }}
|
||||
- --ca-cert-path={{ .Values.webhook.cert.caPath }}/tls.crt
|
||||
{{- end }}
|
||||
- --cert-dir={{ .Values.webhook.cert.path }}
|
||||
- --dns-name={{ $fullName }}-webhook.{{ .Release.Namespace }}.svc
|
||||
- --port={{ .Values.webhook.port }}
|
||||
- --metrics-addr=:8080
|
||||
- --health-addr=:8081
|
||||
- --log-level={{ .Values.logLevel }}
|
||||
{{- range .Values.extrArgs }}
|
||||
{{- range .Values.webhook.extrArgs }}
|
||||
- {{ . }}
|
||||
{{- end }}
|
||||
ports:
|
||||
@@ -65,7 +75,12 @@ spec:
|
||||
protocol: TCP
|
||||
name: health
|
||||
volumeMounts:
|
||||
- mountPath: {{ .Values.webhook.certificate.path }}
|
||||
{{- if not .Values.webhook.cert.certManager.enabled }}
|
||||
- mountPath: {{ .Values.webhook.cert.caPath }}
|
||||
name: ca
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
- mountPath: {{ .Values.webhook.cert.path }}
|
||||
name: cert
|
||||
readOnly: true
|
||||
{{- if .Values.webhook.extraVolumeMounts }}
|
||||
@@ -73,22 +88,10 @@ spec:
|
||||
{{- end }}
|
||||
readinessProbe:
|
||||
httpGet:
|
||||
path: /healthz
|
||||
path: /readyz
|
||||
port: 8081
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 10
|
||||
livenessProbe:
|
||||
httpGet:
|
||||
path: /healthz
|
||||
port: 8081
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 10
|
||||
startupProbe:
|
||||
httpGet:
|
||||
path: /healthz
|
||||
port: 8081
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 10
|
||||
initialDelaySeconds: 20
|
||||
periodSeconds: 5
|
||||
{{ with .Values.webhook.resources }}
|
||||
resources:
|
||||
{{ toYaml . | nindent 12 }}
|
||||
@@ -98,10 +101,16 @@ spec:
|
||||
{{ toYaml . | nindent 12 }}
|
||||
{{ end }}
|
||||
volumes:
|
||||
{{- if not .Values.webhook.cert.certManager.enabled }}
|
||||
- name: ca
|
||||
secret:
|
||||
defaultMode: 420
|
||||
secretName: {{ $fullName }}-webhook-ca
|
||||
{{- end }}
|
||||
- name: cert
|
||||
secret:
|
||||
defaultMode: 420
|
||||
secretName: {{ include "mariadb-operator-webhook.certificate" . }}
|
||||
secretName: {{ $fullName }}-webhook-cert
|
||||
{{- if .Values.webhook.extraVolumes }}
|
||||
{{- toYaml .Values.webhook.extraVolumes | nindent 8 }}
|
||||
{{- end }}
|
||||
|
||||
@@ -0,0 +1,25 @@
|
||||
{{- if not .Values.webhook.cert.certManager.enabled }}
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: {{ include "mariadb-operator.fullname" . }}-webhook-ca
|
||||
labels:
|
||||
{{- include "mariadb-operator-webhook.labels" . | nindent 4 }}
|
||||
mariadb-operator.io/component: webhook
|
||||
{{- with .Values.webhook.cert.secretAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
---
|
||||
apiVersion: v1
|
||||
kind: Secret
|
||||
metadata:
|
||||
name: {{ include "mariadb-operator.fullname" . }}-webhook-cert
|
||||
labels:
|
||||
{{- include "mariadb-operator-webhook.labels" . | nindent 4 }}
|
||||
mariadb-operator.io/component: webhook
|
||||
{{- with .Values.webhook.cert.secretAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
@@ -19,11 +19,9 @@ ha:
|
||||
enabled: false
|
||||
# -- Number of replicas
|
||||
replicas: 3
|
||||
# -- Lease resource name to be used for leader election
|
||||
leaseId: mariadb.mmontes.io
|
||||
|
||||
metrics:
|
||||
# -- Enable prometheus metrics. Prometheus must be installed in the cluster
|
||||
# -- Enable operator internal metrics. Prometheus must be installed in the cluster
|
||||
enabled: false
|
||||
serviceMonitor:
|
||||
# -- Enable controller ServiceMonitor
|
||||
@@ -56,6 +54,9 @@ rbac:
|
||||
# -- Extra arguments to be passed to the controller entrypoint
|
||||
extrArgs: []
|
||||
|
||||
# -- Extra environment variables to be passed to the controller
|
||||
extraEnv: []
|
||||
|
||||
# -- Extra volumes to pass to pod.
|
||||
extraVolumes: []
|
||||
|
||||
@@ -87,31 +88,37 @@ tolerations: []
|
||||
affinity: {}
|
||||
|
||||
webhook:
|
||||
# -- Annotations for webhook configurations.
|
||||
annotations: {}
|
||||
image:
|
||||
repository: ghcr.io/mariadb-operator/mariadb-operator
|
||||
pullPolicy: IfNotPresent
|
||||
# -- Image tag to use. By default the chart appVersion is used
|
||||
tag: ""
|
||||
imagePullSecrets: []
|
||||
certificate:
|
||||
# -- Use cert-manager to issue and rotate the certificate. If set to false, a default certificate will be used.
|
||||
certManager: false
|
||||
# -- Default certificate generated when the chart is installed or upgraded.
|
||||
default:
|
||||
# -- Certificate authority expiration in days.
|
||||
caExpirationDays: 365
|
||||
# -- Certificate expiration in days.
|
||||
certExpirationDays: 365
|
||||
# -- Annotations for certificate Secret.
|
||||
annotations: {}
|
||||
# -- Helm hook to be added to the default certificate.
|
||||
hook: ""
|
||||
ha:
|
||||
# -- Enable high availability
|
||||
enabled: false
|
||||
# -- Number of replicas
|
||||
replicas: 3
|
||||
cert:
|
||||
certManager:
|
||||
# -- Whether to use cert-manager to issue and rotate the certificate. If set to false, mariadb-operator's cert-controller will be used instead.
|
||||
enabled: false
|
||||
# -- Issuer reference to be used in the Certificate resource. If not provided, a self-signed issuer will be used.
|
||||
issuerRef: {}
|
||||
# -- Duration to be used in the Certificate resource,
|
||||
duration: ""
|
||||
# -- Renew before duration to be used in the Certificate resource.
|
||||
renewBefore: ""
|
||||
# -- Annotatioms to be added to webhook TLS secret.
|
||||
secretAnnotations: {}
|
||||
# -- Labels to be added to webhook TLS secret.
|
||||
secretLabels: {}
|
||||
# -- Path where the CA certificate will be mounted.
|
||||
caPath: /tmp/k8s-webhook-server/certificate-authority
|
||||
# -- Path where the certificate will be mounted.
|
||||
path: /tmp/k8s-webhook-server/serving-certs
|
||||
# -- Port to be used by the webhook server
|
||||
port: 10250
|
||||
port: 9443
|
||||
# -- Expose the webhook server in the host network
|
||||
hostNetwork: false
|
||||
serviceMonitor:
|
||||
@@ -136,6 +143,8 @@ webhook:
|
||||
# -- The name of the service account to use.
|
||||
# If not set and enabled is true, a name is generated using the fullname template
|
||||
name: ""
|
||||
# -- Annotations for webhook configurations.
|
||||
annotations: {}
|
||||
# -- Extra arguments to be passed to the webhook entrypoint
|
||||
extrArgs: []
|
||||
# -- Extra volumes to pass to webhook Pod
|
||||
@@ -159,3 +168,71 @@ webhook:
|
||||
tolerations: []
|
||||
# -- Affinity to add to controller Pod
|
||||
affinity: {}
|
||||
|
||||
certController:
|
||||
# -- Specifies whether the cert-controller should be created.
|
||||
enabled: true
|
||||
image:
|
||||
repository: ghcr.io/mariadb-operator/mariadb-operator
|
||||
pullPolicy: IfNotPresent
|
||||
# -- Image tag to use. By default the chart appVersion is used
|
||||
tag: ""
|
||||
imagePullSecrets: []
|
||||
ha:
|
||||
# -- Enable high availability
|
||||
enabled: false
|
||||
# -- Number of replicas
|
||||
replicas: 3
|
||||
# -- CA certificate validity. It must be greater than certValidity.
|
||||
caValidity: 35064h
|
||||
# -- Certificate validity.
|
||||
certValidity: 8766h
|
||||
# -- Duration used to verify whether a certificate is valid or not.
|
||||
lookaheadValidity: 2160h
|
||||
# -- Requeue duration to ensure that certificate gets renewed.
|
||||
requeueDuration: 5m
|
||||
serviceMonitor:
|
||||
# -- Enable cert-controller ServiceMonitor. Metrics must be enabled
|
||||
enabled: true
|
||||
# -- Labels to be added to the cert-controller ServiceMonitor
|
||||
additionalLabels: {}
|
||||
# release: kube-prometheus-stack
|
||||
# -- Interval to scrape metrics
|
||||
interval: 30s
|
||||
# -- Timeout if metrics can't be retrieved in given time interval
|
||||
scrapeTimeout: 25s
|
||||
serviceAccount:
|
||||
# -- Specifies whether a service account should be created
|
||||
enabled: true
|
||||
# -- Automounts the service account token in all containers of the Pod
|
||||
automount: true
|
||||
# -- Annotations to add to the service account
|
||||
annotations: {}
|
||||
# -- Extra Labels to add to the service account
|
||||
extraLabels: {}
|
||||
# -- The name of the service account to use.
|
||||
# If not set and enabled is true, a name is generated using the fullname template
|
||||
name: ""
|
||||
# -- Extra arguments to be passed to the cert-controller entrypoint
|
||||
extrArgs: []
|
||||
# -- Extra volumes to pass to cert-controller Pod
|
||||
extraVolumes: []
|
||||
# -- Extra volumes to mount to cert-controller container
|
||||
extraVolumeMounts: []
|
||||
# -- Annotations to add to cert-controller Pod
|
||||
podAnnotations: {}
|
||||
# -- Security context to add to cert-controller Pod
|
||||
podSecurityContext: {}
|
||||
# -- Security context to add to cert-controller container
|
||||
securityContext: {}
|
||||
# -- Resources to add to cert-controller container
|
||||
resources: {}
|
||||
# requests:
|
||||
# cpu: 10m
|
||||
# memory: 32Mi
|
||||
# -- Node selectors to add to controller Pod
|
||||
nodeSelector: {}
|
||||
# -- Tolerations to add to controller Pod
|
||||
tolerations: []
|
||||
# -- Affinity to add to controller Pod
|
||||
affinity: {}
|
||||
|
||||
@@ -3,8 +3,8 @@ name: piraeus
|
||||
description: |
|
||||
The Piraeus Operator manages software defined storage clusters using LINSTOR in Kubernetes.
|
||||
type: application
|
||||
version: 2.3.0
|
||||
appVersion: "v2.3.0"
|
||||
version: 2.4.1
|
||||
appVersion: "v2.4.1"
|
||||
maintainers:
|
||||
- name: Piraeus Datastore
|
||||
url: https://piraeus.io
|
||||
|
||||
@@ -17,19 +17,19 @@ data:
|
||||
# quay.io/piraeusdatastore/piraeus-server:v1.24.2
|
||||
components:
|
||||
linstor-controller:
|
||||
tag: v1.25.1
|
||||
tag: v1.26.2
|
||||
image: piraeus-server
|
||||
linstor-satellite:
|
||||
tag: v1.25.1
|
||||
tag: v1.26.2
|
||||
image: piraeus-server
|
||||
linstor-csi:
|
||||
tag: v1.3.0
|
||||
tag: v1.4.0
|
||||
image: piraeus-csi
|
||||
drbd-reactor:
|
||||
tag: v1.4.0
|
||||
image: drbd-reactor
|
||||
ha-controller:
|
||||
tag: v1.1.4
|
||||
tag: v1.2.0
|
||||
image: piraeus-ha-controller
|
||||
drbd-shutdown-guard:
|
||||
tag: v1.0.0
|
||||
@@ -38,7 +38,7 @@ data:
|
||||
tag: v0.10
|
||||
image: ktls-utils
|
||||
drbd-module-loader:
|
||||
tag: v9.2.6
|
||||
tag: v9.2.8
|
||||
# The special "match" attribute is used to select an image based on the node's reported OS.
|
||||
# The operator will first check the k8s node's ".status.nodeInfo.osImage" field, and compare it against the list
|
||||
# here. If one matches, that specific image name will be used instead of the fallback image.
|
||||
@@ -54,12 +54,18 @@ data:
|
||||
image: drbd9-almalinux8
|
||||
- osImage: AlmaLinux 9
|
||||
image: drbd9-almalinux9
|
||||
- osImage: Rocky Linux 8
|
||||
image: drbd9-almalinux8
|
||||
- osImage: Rocky Linux 9
|
||||
image: drbd9-almalinux9
|
||||
- osImage: Ubuntu 18\.04
|
||||
image: drbd9-bionic
|
||||
- osImage: Ubuntu 20\.04
|
||||
image: drbd9-focal
|
||||
- osImage: Ubuntu 22\.04
|
||||
image: drbd9-jammy
|
||||
- osImage: Debian GNU/Linux 12
|
||||
image: drbd9-bookworm
|
||||
- osImage: Debian GNU/Linux 11
|
||||
image: drbd9-bullseye
|
||||
- osImage: Debian GNU/Linux 10
|
||||
@@ -69,25 +75,25 @@ data:
|
||||
base: registry.k8s.io/sig-storage
|
||||
components:
|
||||
csi-attacher:
|
||||
tag: v4.4.2
|
||||
tag: v4.5.0
|
||||
image: csi-attacher
|
||||
csi-livenessprobe:
|
||||
tag: v2.11.0
|
||||
tag: v2.12.0
|
||||
image: livenessprobe
|
||||
csi-provisioner:
|
||||
tag: v3.6.2
|
||||
tag: v4.0.0
|
||||
image: csi-provisioner
|
||||
csi-snapshotter:
|
||||
tag: v6.3.2
|
||||
tag: v7.0.1
|
||||
image: csi-snapshotter
|
||||
csi-resizer:
|
||||
tag: v1.9.2
|
||||
tag: v1.10.0
|
||||
image: csi-resizer
|
||||
csi-external-health-monitor-controller:
|
||||
tag: v0.10.0
|
||||
tag: v0.11.0
|
||||
image: csi-external-health-monitor-controller
|
||||
csi-node-driver-registrar:
|
||||
tag: v2.9.1
|
||||
tag: v2.10.0
|
||||
image: csi-node-driver-registrar
|
||||
{{- range $idx, $value := .Values.imageConfigOverride }}
|
||||
{{ add $idx 1 }}_helm_override.yaml: |
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@@ -152,3 +152,27 @@ webhooks:
|
||||
resources:
|
||||
- linstorsatelliteconfigurations
|
||||
sideEffects: None
|
||||
- admissionReviewVersions:
|
||||
- v1
|
||||
clientConfig:
|
||||
service:
|
||||
name: '{{ include "piraeus-operator.fullname" . }}-webhook-service'
|
||||
namespace: '{{ .Release.Namespace }}'
|
||||
path: /validate-storage-k8s-io-v1-storageclass
|
||||
{{- if not .Values.tls.certManagerIssuerRef }}
|
||||
caBundle: {{ $ca }}
|
||||
{{- end }}
|
||||
failurePolicy: {{ .Values.webhook.failurePolicy }}
|
||||
timeoutSeconds: {{ .Values.webhook.timeoutSeconds }}
|
||||
name: vstorageclass.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- storage.k8s.io
|
||||
apiVersions:
|
||||
- v1
|
||||
operations:
|
||||
- CREATE
|
||||
- UPDATE
|
||||
resources:
|
||||
- storageclasses
|
||||
sideEffects: None
|
||||
|
||||
@@ -1,9 +1,11 @@
|
||||
apiVersion: v2
|
||||
appVersion: 1.21.1
|
||||
description: CloudNativePG Helm Chart
|
||||
appVersion: 1.22.2
|
||||
description: CloudNativePG Operator Helm Chart
|
||||
home: https://cloudnative-pg.io
|
||||
icon: https://raw.githubusercontent.com/cloudnative-pg/artwork/main/cloudnativepg-logo.svg
|
||||
keywords:
|
||||
- operator
|
||||
- controller
|
||||
- postgresql
|
||||
- postgres
|
||||
- database
|
||||
@@ -14,4 +16,4 @@ name: cloudnative-pg
|
||||
sources:
|
||||
- https://github.com/cloudnative-pg/charts
|
||||
type: application
|
||||
version: 0.19.1
|
||||
version: 0.20.2
|
||||
|
||||
File diff suppressed because one or more lines are too long
File diff suppressed because it is too large
Load Diff
File diff suppressed because it is too large
Load Diff
@@ -31,8 +31,9 @@ spec:
|
||||
{{- include "cloudnative-pg.selectorLabels" . | nindent 6 }}
|
||||
template:
|
||||
metadata:
|
||||
{{- with .Values.podAnnotations }}
|
||||
annotations:
|
||||
checksum/config: {{ include (print $.Template.BasePath "/config.yaml") . | sha256sum }}
|
||||
{{- with .Values.podAnnotations }}
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
|
||||
@@ -0,0 +1,12 @@
|
||||
{{- if .Values.monitoring.grafanaDashboard.create -}}
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: {{ .Values.monitoring.grafanaDashboard.configMapName }}
|
||||
namespace: {{ default .Release.Namespace .Values.monitoring.grafanaDashboard.namespace }}
|
||||
labels:
|
||||
{{ .Values.monitoring.grafanaDashboard.sidecarLabel }}: {{ .Values.monitoring.grafanaDashboard.sidecarLabelValue | quote }}
|
||||
data:
|
||||
cnp.json: |-
|
||||
{{ .Files.Get "monitoring/grafana-dashboard.json" | indent 6 }}
|
||||
{{- end -}}
|
||||
@@ -95,6 +95,26 @@
|
||||
"monitoring": {
|
||||
"type": "object",
|
||||
"properties": {
|
||||
"grafanaDashboard": {
|
||||
"type": "object",
|
||||
"properties": {
|
||||
"configMapName": {
|
||||
"type": "string"
|
||||
},
|
||||
"create": {
|
||||
"type": "boolean"
|
||||
},
|
||||
"namespace": {
|
||||
"type": "string"
|
||||
},
|
||||
"sidecarLabel": {
|
||||
"type": "string"
|
||||
},
|
||||
"sidecarLabelValue": {
|
||||
"type": "string"
|
||||
}
|
||||
}
|
||||
},
|
||||
"podMonitorEnabled": {
|
||||
"type": "boolean"
|
||||
}
|
||||
|
||||
@@ -139,6 +139,16 @@ affinity: {}
|
||||
monitoring:
|
||||
# -- Specifies whether the monitoring should be enabled. Requires Prometheus Operator CRDs.
|
||||
podMonitorEnabled: false
|
||||
grafanaDashboard:
|
||||
create: false
|
||||
# -- Allows overriding the namespace where the ConfigMap will be created, defaulting to the same one as the Release.
|
||||
namespace: ""
|
||||
# -- The name of the ConfigMap containing the dashboard.
|
||||
configMapName: "cnpg-grafana-dashboard"
|
||||
# -- Label that ConfigMaps should have to be loaded as dashboards.
|
||||
sidecarLabel: "grafana_dashboard"
|
||||
# -- Label value that ConfigMaps should have to be loaded as dashboards.
|
||||
sidecarLabelValue: "1"
|
||||
|
||||
# Default monitoring queries
|
||||
monitoringQueriesConfigMap:
|
||||
|
||||
@@ -1,9 +1,18 @@
|
||||
#!/bin/sh
|
||||
VERSION=2
|
||||
set -o pipefail
|
||||
set -e
|
||||
|
||||
run_migrations() {
|
||||
return 0
|
||||
if ! kubectl get configmap -n cozy-system cozystack-version; then
|
||||
kubectl create configmap -n cozy-system cozystack-version --from-literal=version="$VERSION" --dry-run=client -o yaml | kubectl create -f-
|
||||
fi
|
||||
current_version=$(kubectl get configmap -n cozy-system cozystack-version -o jsonpath='{.data.version}') || true
|
||||
until [ "$current_version" = "$VERSION" ]; do
|
||||
echo "run migration: $current_version --> $VERSION"
|
||||
scripts/migrations/$current_version
|
||||
current_version=$(kubectl get configmap -n cozy-system cozystack-version -o jsonpath='{.data.version}')
|
||||
done
|
||||
}
|
||||
|
||||
flux_is_ok() {
|
||||
@@ -18,6 +27,9 @@ install_basic_charts() {
|
||||
|
||||
cd "$(dirname "$0")/.."
|
||||
|
||||
# Run migrations
|
||||
run_migrations
|
||||
|
||||
# Install namespaces
|
||||
make -C packages/core/platform namespaces-apply
|
||||
|
||||
@@ -26,20 +38,12 @@ if ! flux_is_ok; then
|
||||
install_basic_charts
|
||||
fi
|
||||
|
||||
# Run migrations
|
||||
run_migrations
|
||||
|
||||
# Reconcile Helm repositories
|
||||
kubectl annotate helmrepositories.source.toolkit.fluxcd.io -A -l cozystack.io/repository reconcile.fluxcd.io/requestedAt=$(date +"%Y-%m-%dT%H:%M:%SZ") --overwrite
|
||||
|
||||
# Install platform chart
|
||||
make -C packages/core/platform apply
|
||||
|
||||
# Flush kubeapps cache
|
||||
if kubectl wait --for=condition=ready -n cozy-dashboard pod/dashboard-redis-master-0 --timeout=1s; then
|
||||
kubectl exec -ti -n cozy-dashboard dashboard-redis-master-0 -- sh -c 'redis-cli -a "$REDIS_PASSWORD" flushdb'
|
||||
fi
|
||||
|
||||
# Reconcile platform chart
|
||||
trap 'exit' INT TERM
|
||||
while true; do
|
||||
|
||||
8
scripts/migrations/1
Executable file
8
scripts/migrations/1
Executable file
@@ -0,0 +1,8 @@
|
||||
#!/bin/sh
|
||||
|
||||
if kubectl get -n cozy-mariadb-operator secret/mariadb-operator-webhook-cert; then
|
||||
kubectl annotate -n cozy-mariadb-operator secret/mariadb-operator-webhook-cert meta.helm.sh/release-namespace=cozy-mariadb-operator meta.helm.sh/release-name=mariadb-operator
|
||||
kubectl label -n cozy-mariadb-operator secret/mariadb-operator-webhook-cert app.kubernetes.io/managed-by=Helm
|
||||
fi
|
||||
|
||||
kubectl create configmap -n cozy-system cozystack-version --from-literal=version=2 --dry-run=client -o yaml | kubectl apply -f-
|
||||
Reference in New Issue
Block a user